Abstract
The cypherpunks were 1990s digital activists who challenged White House policies aiming to prevent the emergence of unregulated digital cryptography, an online privacy technology capable of frustrating government surveillance. Whilst the cypherpunk’s ideology, which is predominantly the output of Timothy C. May, is well understood, less is known about the composition of the cypherpunk’s community. This article builds on past studies by Rid and Beltramini by using the cypherpunk’s mail list archive to profile the most active and influential cypherpunks. This study confirms the May-derived ideology is broadly, though not entirely, representative of the cypherpunk community. This article assesses the cypherpunks were a highly educated, mostly libertarian community permeated by aspects of anarchism which arose from a societal disaffiliation inherited from the counterculture. This article further argues that the cypherpunks were also influenced by the hacker ethic and dystopian science fiction.
Introduction
The cypherpunks were a group of privacy activists who in the 1990s helped establish the use of unregulated digital cryptography within the United States. Digital privacy, better phrased as privacy in the digital age given the inexorable digital-physical convergence, is achieved principally via digital security. When considering the base elements of digital security, Professor Keith Martin comments that, “cryptography is pretty much the only game in town” (Martin, 2020, p. 2). Cryptography allows not only for a host of vital applications within our everyday lives, such as secure financial transactions, but also for capabilities the cypherpunks hoped would undermine the State (May, 1988). Such encryption-dependent technologies include: block-chains, which can place financial transactions beyond the government’s ability to monitor and tax; whistleblowing platforms, capable of facilitating leaks whilst protecting the whistleblower; and anonymity networks, which can obfuscate a citizen’s physical location.
The cypherpunks helped shape our Internet. Beltramini comments they were, “perhaps the single most effective grassroots organization in history dedicated to protecting freedom in cyberspace” (Beltramini, 2020, p. 1). However, Dahlberg argues that cyber-libertarian visions of the future, such as those held by the cypherpunks, had mostly dissipated by 2000, he comments that by then the Internet was, “seen as part and parcel of “everyday life” – simply an extension of existing social systems, rather than being a revolutionary medium transcending offline political and economic constraints” (2010, p. 333). However, Dahlberg’s assessment fails to account for the significant 1990s cryptographic advances made by the citizenry, which included weakening export controls, defeating the Clinton administration’s attempts to further regulate cryptography, and establishing the foundation for current technologies such as crypto-currencies. Today, law enforcement does not consider unregulated encryption as a tolerable status quo as its use hinders their access to suspect’s data. [1] In 2020 alone, two bills were introduced in Congress which could outlaw encryption not containing a government access method (commonly referred to as a “back door”) (United States Congress, 2020; United States Senate, (2020). When the Clinton administration sought to include a back door within encryption technologies in the 1990s, the cypherpunks led the successful battle to defeat government policy, thus helping to establish unregulated cryptography. The cypherpunk ideology now influences a new generation of digital privacy activists. [2] These new activists are responsible for challenging today’s government policies to mandate encryption back doors.
It is important we understand the community which last successfully challenged the State’s attempt to regulate cryptography so that ongoing debates are informed by an accurate characterization of those who established today’s status quo. This article builds on the cypherpunk studies of Rid 2016 and Beltramini (2020) by using the cypherpunk mail list archive to profile the broader cypherpunk community. This profiling indicates that the cypherpunks were a highly educated, primarily libertarian community permeated by aspects of anarchism which arose from a societal disaffiliation inherited from the counterculture. The profiling further indicates that the cypherpunks objectives were directed to minimize, or even remove the State from public life, and that they were influenced by the hacker ethic and dystopian science fiction.
Literature review
Literature on the cypherpunks is sparse. Whilst topics in which the cypherpunks were influential such as the crypto wars, crypto currencies, and leaking platforms have received attention, most research has not focused on the community at the genesis of these technologies. [3]
The most extensive academic study of the cypherpunks is a chapter within Rid’s book The Rise of the Machines, which establishes the cypherpunks in their wider cultural context. Beltramini contributes an article dedicated to the ideological genesis of the cypherpunks which, whilst helpful in contextualizing aspects of the counterculture and punk movements of mid-twentieth century San Francisco, the region from where the cypherpunks emerged, spends little time exploring the cypherpunk community itself. Beltramini concedes more work is needed on the cypherpunks, this article addresses that gap (2020, p. 2). Dahlberg provides a useful analysis of the broader cyber-libertarianism movement, though the cypherpunks are not the principal subjects of his study (2010). Within popular literature, the two key texts are Levy’s 2001 Crypto, and Andy Greenberg’s This Machine Kill Secrets. Levy’s work is more general, focusing of the cypherpunk’s role in the crypto wars, whilst Greenberg studies cypherpunk Julian Assange’s development of Wikileaks, a cryptography-infused whistleblowing platform.
Methodology
The core data set used for this research are the cypherpunk’s online posts created between 1992 and 1998 within their digital club house, known as the mail list (Cypherpunk Mail List Archives, (1992–1998). [4] The mail list contains over 98,000 posts from at least a thousand contributors.[5] To profile the individual members of the cypherpunk mail list, the author has combined two purposive sampling methods: typical case sampling and extreme/deviant case sampling (Palys, [2008], p. 697). Most posts are made by a core of around 200 users, therefore a sample size of 20% of these individuals, 40 cypherpunks, is assessed as sufficient to achieve theoretical saturation. To select these individuals the author firstly identified the most active members on the forum to generate population insights (typical case sampling). The author then identified users who, whilst less active on the mail list, were ideologically significant, historically significant, or bridged the cypherpunks to the larger digital rights community (extreme/deviant case sampling). The author’s selection of these individuals was based on analysis of the mail list’s first nine months (4,500) posts, sampling of threads on significant digital privacy topics (e.g. encryption-related government policies, development of encryption technologies) throughout the mail list’s existence, and examination of the secondary literature. Details of the individuals sampled, and an accompanying taxonomy can be found in the appendices of this article. The sampled cypherpunks allow a profiling of the individuals, their political ideologies, and their backgrounds. The author has augmented posts from this sample set with the wider population when considering the ideology of the broader community (e.g. posts relating to specific literary influences). The author’s assessment is also informed by analysis of the cypherpunk’s doctrinal documents. [6]
Analysis
The Cypherpunk’s mail list
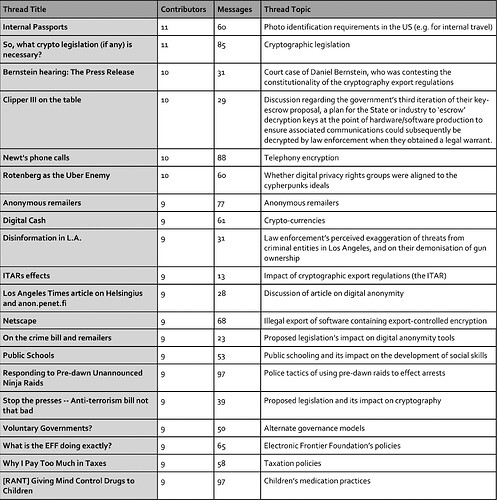
Mailing lists were a vehicle for online discussion during the late 1980s and 1990s. Typically, one would subscribe to a mail list by emailing the list administrator. The Cypherpunk’s mail list was unmoderated, in-keeping with the collective’s distrust of structures which empowered any single source of authority. The mail list was organized by threads, which were derived from email subject lines. Once a user posted to the mail list all subscribers would receive the message, meaning users were often overwhelmed by the volume of posts, for example, in 1994 over 15,000 messages were posted to the mail list creating a poor signal to noise ratio. Vociferous debate often descended into fractious exchanges and outright hostility, a series of such exchanges were known as “flame wars,” today such exchanges would broadly be labelled as “trolling.” Some users (six of the sampled cypherpunks, and many more within the broader community) posted anonymously under “nyms” (pseudonyms). Figure 1 shows the top 20 threads to which the sampled cypherpunks contributed.
Figure 1. Top 20 Cypherpunk Threads.
This mixture of threads, ranging from technical topics (e.g. “anonymous remailers”), crypto-anarchy subjects, political issues and further miscellany conveys the breadth of discourse. However, even the most popular threads are typically short lived, normally enduring for less than a week, though some do persist for months. The top threads had eleven or fewer contributors, though this does not account for wider cypherpunk inclusion outside the sample set. To give a sampling of these topics a small number of these threads are worthy of brief examination. The thread “[RANT] Giving Mind Control Drugs to Children,” explores the practice of giving medicine to children with psychological issues. As with many topics on the mail list, it was related back to perceived government overreach, Duncan Frissell posted:
My real problem with the whole thing is that Ritalin is being prescribed by government employees in most cases. It thus constitutes behavior modification of the population by the government which is certainly a human rights violation. It is arguably a First Amendment violation for the government to chemically prevent you from expressing yourself in certain ways. They should not even be allowed to advocate such treatment. (Frissell, [1996])
The “Netscape” thread discusses the discovery on a domestic server of copies of Netscape software equipped with stronger encryption than was legally exportable (Anonymous Poster, [1996] . [7] The cypherpunks debated whether they should try to export the code overseas as an act of civil disobedience, or to generate a legal case where the exporter would appear as a martyr battling unfair laws, Vladimir Z. Nuri commented:
by creating a very large, glaring, and visceral public spectacle of the government cracking down on crypto, the resulting outcry could be absolutely enormous and resonate throughout the entire population. it would be a vivid portrayal of what the government has been doing quietly and secretly for decades, and perhaps the public might finally understand what is going on. (Bell, [1996]; Nuri, [1996])
The debate seemed to conclude such an action would be an unwise, as Perry Metzger implored the more belligerent cypherpunks to, “Leave ‘em alone,” as Netscape were generally considered a pro-crypto force.
Doctrine
The cypherpunks formed in September 1992 (May, 1994b, 1.2). Timothy C. May was the cypherpunk’s chief ideologue, Beltramini comments, “Most of the self-produced cypherpunk literature is in fact the brainchild of a single mind – that of Tim May” (Beltramini, 2020, p. 2). May published his crypto anarchist manifesto in 1988, in which he wrote, “A specter is haunting the modern world, the specter of crypto anarchy.” May’s manifesto argued the technology for a “social and economic revolution” was now emerging, and the coming decade would bring sufficient computing power to make the revolution, “economically feasible and essentially unstoppable.” Just as the invention of the printing press eroded the power of the medieval guilds, May believed cryptography would alter the nature of commerce and governance. Implicit in May’s writings was that the government’s ability to collect taxes and surveil its citizens would severely diminish once their interactions were guarded by cryptography. May believed:
The State will of course try to slow or halt the spread of this technology [cryptography], citing national security concerns, use of the technology by drug dealers and tax evaders, and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be trade[d] freely and will allow illicit and stolen materials to be traded. An anonymous computerised market will even make possible abhorrent markets for assassinations and extortion.
In 1996, Jim Bell took May’s ideas further by producing detailed plans on how anonymous digital assassination markets could be developed and operated using encryption technologies, and how they could catalyse an anarchic state (Bell, 1997). For the cypherpunks, whilst cryptography could facilitate deeds they found immoral, such as child abuse, the citizenries ability to protect itself with encryption was akin to its constitutional right to gun ownership (May, 1994b. Whilst both guns and encryption could be used to immoral ends, they were considered by the cypherpunks as the citizenries last defence against a potentially tyrannical government, Russell Whitaker comments, “arguments for the right to keep and bear arms can often be directly mapped onto […] the right to keep and use pkeys [private encryption keys].” (Whitaker, 1992). Rid comments that during the period of the cypherpunks, “intellectuals were inebriated by the simultaneous emergence of two revolutionary forces: personal computers and the Internet,” and that the cypherpunks believed, “The state […] would lose a good deal of its coercive power” (Rid, 2016, Chapter 7).
During the cypherpunk’s first physical meeting Jude Milhon, a guest, seasoned hacker, and activist who once wrote a how-to guide for “online revolution” joked, “you guys are just a bunch of cypherpunks,” according to May the name was “adopted immediately” (May, 1994b, 2.4.9; Milhon, n.d.. The name was a play on the cyberpunk genre which combines science fiction with hackers and cyberspace. Cyberpunk novels include William Gibson’s Neuromancer, the inspiration for the Matrix movies. Such movies typically depict hackers who are victimised by oppressive regimes in the physical world, but who flourish in cyberspace, often finding ways to use their intellect to outsmart dictatorial overlords. Beltramini argues cyberpunk hero was a hacker, “who lives on the edge of society, an alienated loner in a dystopic society” (2020, p. 12). However, whilst alienation in youth for hackers is common, Beltramini’s characterization discounts the strong communal bounds that often exists within adult hacking communities, such as that of the cypherpunks. When it came to aesthetics, May acknowledges the cypherpunks were, “about as punkish as most of our cyberpunk cousins are, which is to say, not very” (May, 1994b, 2.4.9). Some cypherpunks believed they should re-brand themselves, that talk of anarchy was, “not helpful to the cause,” and, “Middle America will be turned off by the hippie radicals in t-shirts, leather jackets, sandals, and beards” (May, 1993). They argued that unless the cypherpunks could speak the language of the “suits” their message would fall on deaf ears. Alternative names for their group such as “Cryptographic Research Association” or “Cryptography Privacy” were suggested, but May demurred:
I fully agree with many of you that the name “Cypherpunks” has some, shall we say, unusual connotations […] But the name has undeniable appeal to many, and certainly grabs a lot of attention. It seems improbable that some staid name like “Northern California Cryptography Hobbyists Association” would’ve gotten much attention. (May, [1993a])
Objectives
Absent official leadership, shared goals bound the cypherpunks, their focus on these objectives are reflected in the mail list archives. Cypherpunk strategic objectives encompass four areas:
- Unregulated citizen encryption access
- Anonymous communications
- Freedom to conduct anonymous economic transactions (crypto currencies)
- Development of leaking platforms to constrain government power
The primary objective of the cypherpunks was that encryption should be unencumbered by governmental regulations. The cypherpunks believed ubiquitous encryption would prevent the state surveilling its citizen’s digital data and allow commerce to migrate online (May, 1988). When the cypherpunks discovered the Clinton administration had created an email account to solicit policy inputs from citizens in 1993, Marc Ringuette suggested the following be sent on behalf of their group:
Dear President Clinton,
Freedom for the bits! We will not rest until each bit is free to determine its own natural orientation without outside coercion. The good news is, you don’t need to do anything at all; merely get out of the way of the free market, and the bits will free themselves.
Best regards,
The Cypherpunks. (Ringuette, 1993)
With divergent opinions on the desired political implications of ubiquitous encryption, alias user Larry Detweiler notes the only, “major consensus of the cypherpunks is the commitment to cryptography and the believe that it should be unregulated” (Detweiler, 1993). Anonymity was a closely related privacy objective, as it would allow minority opinions, such as those of the cypherpunks, to be heard without fears of majority reprisals. The US boasts a rich history of anonymity. For instance, in the late 1780s eighty-five essays supporting the recently drafted ratification of the US constitution were published in newspapers by Founding Fathers James Madison, Alexander Hamilton and John Jay. All were authored under the pseudonym “Publius,” and collectively became known at the Federalist Papers (United States Library of Congress, n.d.). Perhaps no stronger argument could be made for the Father’s feelings towards anonymity. The cypherpunks considered anonymity the shield of the citizenry, for it was their corporeal forms, rather than their ideas, which were vulnerable to State coercion. Ideas could be suppressed, but never destroyed. Cypherpunk co-founder Eric Hughes comments cyberspace anonymity was intended to, “create immunity from these [physical] threats” (May, 1994b, 6.7.2).
David Chaum, considered the father of crypto currencies, first articulated the surveillance implications of digital transactions in his 1985 article Security Without Identification, Transaction Systems to make Big Brother Obsolete, the title of which conveys Chaum’s political leanings. Chaum argued:
The foundation is being laid for a dossier society, in which computers could be used to infer individuals’ life-styles, habits, whereabouts, and associations from data collected in ordinary consumer transactions. (p. 1030)
Chaum, a Professor at New York and later California University, grew up in the midst of the counterculture, as a student he left his UCLA graduate programme in disagreement with its military funding (Greenberg, 2012, Chapter 2). Rid comments, “Chaum’s idea [for crypto-currencies] was magically simple and powerful,” however, the concepts were also far beyond the technical capabilities of the era (Rid, 2016, Chapter 7). Chaum was not a cypherpunk, but his writings form an indispensable book in their gospel, and Hughes worked for him in Amsterdam (Slater, 1997). Amongst Chaum’s most cogent observations was:
Computerization is robbing individuals of the ability to monitor and control the ways information about them is used. Already, public and private sector organizations acquire extensive personal information and exchange it amongst themselves. (Chaum, 1985a, p. 1030)
This trend of people not knowing their data is secure, Chaum posited, could have a, “chilling effect,” causing them to, “alter their observable behaviours” (Chaum, 1985a, p. 1030). Chaum argued this behaviour modification would produce an effect on society similar to that described by the Jeremy Bentham’s panopticon prison, designed in 1791 (Bentham, 1843). Efficiency motivated Bentham’s design – he wanted to enable a small number of prison guards to monitor a large number of inmates. Bentham conceived of a circular building in which the cells would be at the circumference and the guard tower in the centre, where by the use of, “blinds and other contrivances,” the guards would be concealed from their prisoners, this would promote, “the sentiment of a sort of omnipresence” (Bentham, 1843). The inmates would never know when they were being watched, therefore they would modify their behaviour on the assumption of constant surveillance. Chaum believed a dossier society would render this same effect. Digital transactions expanded the dangers of the dossier society to “an unprecedented extent,” Chaum wrote in 1985 (Chaum, 1985b). Seven years later, May warned the trend towards a, “cashless society represents the greatest threat,” he argued it would be, “worse that [than] Orwells’ worst should it become government run” (May, 1992). May told the cypherpunks they must act to prevent this fear becoming reality. Crypto currencies appealed to the cypherpunks as their operating models were decentralised, relying on no intermediaries such as banks. In combination with encryption and the anonymity infrastructure, crypto currencies would allow transactions to occur between two parties without the state’s knowledge. If the state could not see transactions, it could not levy taxes, nor build a dossier society. Therefore, the cypherpunks believed crypto currencies could clog the arteries fuelling the body politic. The cypherpunks posited that without taxes, the state’s beating heart would fall silent, and the era of crypto anarchy could begin (May, 1994b, 17.6.1).
Julian Assange’s essay, Conspiracy as a form of Governance, evangelising the transparency and destructive effects whistleblowing catalyses, articulates the impact for which the cypherpunks were striving:
The more secretive or unjust an organization is, the more leaks induce fear and paranoia in its leadership and planning coterie. This must result in minimization of efficient internal communications mechanisms […] and consequent system-wide cognitive decline resulting in decreased ability to hold onto power as the environment demands adaption. (Assange, 2006)
Assange asks the reader to imagine what would become of a conspiratorial organisation, such as, in his example, the National Democratic or Republican Parties, if so in fear of leaks they were, they eschewed emails and telephones thus restricting their collaborative abilities:
An authoritarian conspiracy that cannot think is powerless to preserve itself against the opponents it induces. When we look at an authoritarian conspiracy as a whole, we see a system of interacting organs, a beast with arteries and veins whose blood may be thickened and slowed until it falls, stupefied; unable to sufficiently comprehend and control the forces in its environment. (Assange, 2006)
Years after writing this essay, Assange’s Wikileaks played a central role in publishing stolen data from the 2016 Clinton campaign, which likely inculcated at least some institutional paranoia degrading the organisation’s ability to collaborate. Assange believed leaking could frustrate current government abuses and be a defence against future tyrants (Assange, 2006)).
The cypherpunks believed that together, encryption, anonymity, crypto currencies and leaking platforms would provide them the ability to re-shape the world.
The cypherpunks defined themselves as being outside the communities of lobbyists, think tanks and protest movements. The cypherpunks preached direct action; they were a digital insurgency. Whilst digital rights groups such as the Electronic Frontier Foundation lobbied for government recognition of traditional rights in the digital domain, the cypherpunks would create encryption tools to render government policies moot, embodying Lessig’s later pithy assessment that, “code is law” (Lessig, 2006). The philosophy of this approach is articulated in Hughes (1993) Cypherpunk Manifesto:
Cypherpunks write code.
We know that someone has to write software to defend privacy, and since we can’t get privacy unless we all do, we’re going to write it.
We publish our code so that our fellow Cypherpunks may practice and play with it. Our code is free for all to use, worldwide.
We don’t much care if you don’t approve of the software we write.
We know that software can’t be destroyed and that a widely dispersed system can’t be shut down. (Hughes, 1993)
But the “Cypherpunks write code” slogan should not be taken literally, explains Sandy Sandfort, “‘to write code’ means to take unilateral effective action as an individual. That may mean writing actual code, but it could also mean dumpster diving” (May, 1994b, 4.5.3). [8] May explains the phrase actually means to aspire to, “technology and concrete solutions over bickering and chatter” (May, 1994b, 2.4.17). However, as a direct action group, all were expected to contribute with whatever skills they possessed.
Profiling
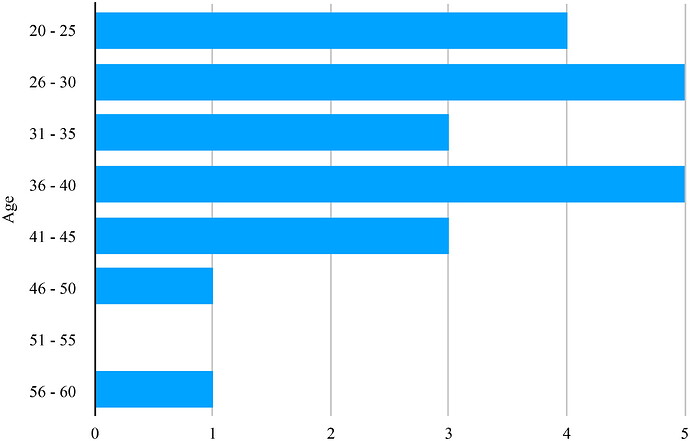
The cypherpunks community can be profiled by analyzing the mail list and enriching this data with information from sources such as LinkedIn and personal websites. Figure 2 shows estimated ages of the sampled cypherpunks on 1 Jan 1993, for the 22 subjects on whom data could be acquired. In some cases, years of birth are estimated by assuming the subject was 18 when they matriculated.
Figure 2. Cypherpunk’s Estimated Ages.
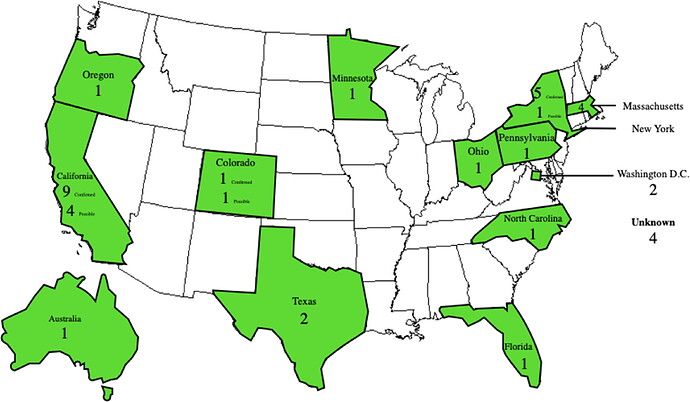
The average age is 33.7; the median age is 33. The youngest was Jim Choate, at 20 years of age, with Peter Junger being the oldest at 57. Given protest culture is often associated with university students, it is surprising such a small proportion of the cypherpunks represented this demographic. The location, or possible location, for 36 of the 40 sampled cypherpunks was identified. Figured 3 shows the sample set’s global dispersion, where location confidence is not certain descriptors of “confirmed” and “possible” are used.
Figure 3. Cypherpunk’s Locations.
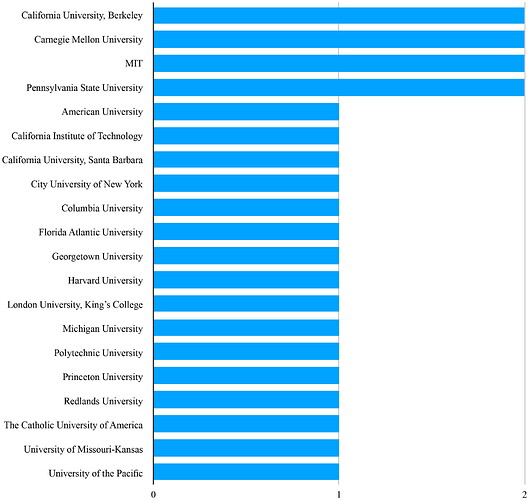
Only Assange lived outside the US. Predictably, the largest concentration of the cypherpunks were located in California, the heart of the global technology industry, and the location where the first physical cypherpunk meetings occurred. However, overall the balance between confirmed west coast (10) and east coast (13) is reasonably balanced. This finding presents a new area for research: why were so many physically removed from the local Beltramini credits for the ideological incubator of crypto anarchism, San Francisco, drawn to its movement? Post-secondary education data for 24 of the cypherpunks has been identified: 12 held bachelor’s degrees, 6 master’s degrees, 4 held legal doctorates, and 2 held PhDs. Seven of the cypherpunk’s qualifications were in computer science, five held law degrees, with further fields of study including mathematics, chemistry, business, engineering, and physics. The surprising number of lawyers is accounted for by either a pre-existing interest in technology, or a professional interest in civil liberties law, through which the subjects were introduced to digital rights and the cypherpunks. There are no strong correlations in the educational institutions attended as highlighted by Figure 4.
Figure 4. Cypherpunk’s Alma Maters.
This data is surprising, as one would have expected a stronger concentration at institutions such as MIT, Santa Barbara and Berkeley, which were known for their computer science programmes and liberal politics. One would also expect a more pronounced west coast concentration, yet the sample set are broadly distributed – again, this challenges the depth of the cypherpunk’s connectivity to San Francisco. Twenty cypherpunks were employed within the technology industry, five within the field of law, with others employed in fields such as architecture, journalism and mathematics, and two were students.
The data shows an expected technology industry bias. Rid comments within the list, “only 10 percent of the cypherpunks wrote code” (Rid, 2016, Chapter 7), however, analysis indicates 35 of the sampled cypherpunks were technologists, whilst 23 were cryptographers. Of those outside the technical fields many had an early interest in technology, or had developed an interest in technology as a result of their profession. For instance, Junger was a law professor who believed that in the digital world attorney-client privilege required the use of encryption (Vasvari & Scarselli, 1996). This finding suggests the most active and influential members of the cypherpunks were often coders or cryptologists, a much higher percentage than perhaps Rid finds in the broader, and less impactful, cypherpunk community.
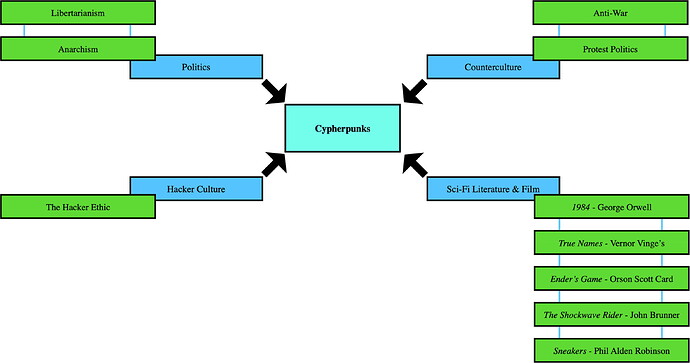
Influences
Analysis of the mail list indicates that a number of influences, depicted in Figured 5, contributed to the cypherpunk’s ideology.
Figure 5. Cypherpunk’s Influences.
Politics
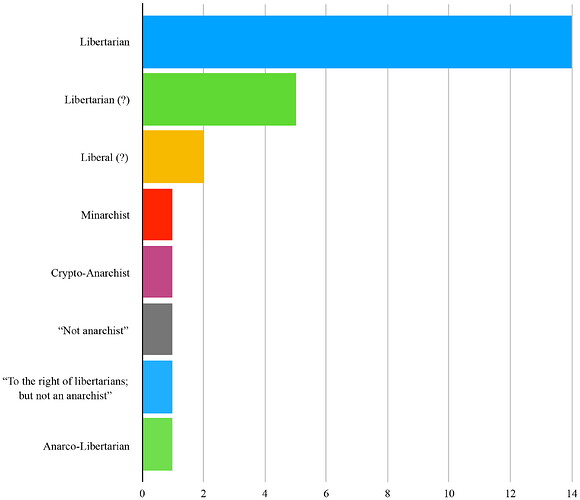
The majority of the cypherpunks were anti-establishment. May comments there were, “a lot of radical libertarians [and] some anarcho-capitalists” (May, 1994b, 1.2). In February 1993, May estimated fifty percent of the list were “strongly libertarian/anarchist” whilst a further twenty percent were liberal or leftist, the rest of the group’s composition was unknown (May, 1993b). On another occasion, May observed additional political orientations included, “anarcho-syndicalists, anarcho-capitalists, Neo-Pagans, Christian Fundamentalists, and maybe even a few unreconstructed Communists” (May, 1994a). Figured 6 shows the political ideology for the sampled cypherpunks, 26 of whom professed their ideologies on the mail list (“?” represents where ideology is strongly suggested, but not avowedly disclosed).
Figure 6. Cypherpunk’s Political Philosophies.
Unsurprisingly of a group that sought to develop cryptographic technologies to empower the individual over the State, most of the sampled cypherpunks were libertarians. This supports popular perception of the cypherpunks as a libertarian movement. However, some cypherpunks had a history of activism and considered themselves liberals rather than libertarians. For instance, Phil Zimmermann was an anti-nuclear protestor who was twice arrested for his part in demonstrations (Dexheimer, 1993).
Political categorisation for the cypherpunks as a cohort is challenging, as they represent a number of ideologies. The cypherpunks are perhaps best classified as a representation of the radical right. However, they are liberal in a conventional sense, for instance in their views about freedom of movement, and are not right wing in a restrictive or partisan way; their ideology is about intellectual endeavour, not political sectarianism or national populism, but they are a form of radical right and are atypical of the radical right as they are highly educated intellectuals. For those of the anarchic and libertarian disposition there was a desire to, in May’s words, “undermine the so-called democratic governments of the world” (May, 1994b, 2.13.6). Libertarians believe the most important political value is liberty, rather than democracy (Boaz, 2015). They feel should the majority be uneducated or unenlightened, the tyranny of the majority can equal the tyranny of a dictator (Hospers, 1971). Libertarians see taxation as the most potent non-lethal weapon at the democrat’s disposal (Hospers, 1971, p. 183). However, the “ultimate evil” is considered the government’s monopoly of violence. Libertarians believe each person should be permitted to live by their own choices, provided they do not attempt to prevent others from doing the same. From the libertarian’s perspective the gravest crimes in history have been perpetrated by governments, often as a result of their deliberate policies (Hospers, 1971, pp. 2–3). Assange had the following C.S. Lewis quote in his signature block in late 1996 evidencing this philosophy, “Of all tyrannies a tyranny sincerely exercised for the good of its victims may be the most oppressive. It may be better to live under robber barons than under omnipotent moral busybodies.” The cypherpunks also believed the governments of the world had caused greater suffering than any other force, Sandfort posted to the mail list, “governments – primarily through the use of their militaries – have killed, by some counts 170,000,000, men, women and children in this century alone. Hardly the guardians of freedom, in my opinion” (1996).
For the anarcho-capitalists, and some libertarians, there was frustration their tax dollars were being spent in sustaining those they believed less productive or able than themselves, May once spoke of the, “the dirt people clamoring for more handouts” (Greenberg, 2012, Chapter 2). Libertarians argue they should not be compelled to aid their fellow citizens, they believe to provide such aid is a choice individuals should make, rather than by being compelled into doing so via taxation (Hospers, [1971, p. 11). May argues crypto anarchy would resolve the issue of supporting an unproductive majority:
Crypto anarchy means prosperity for those who can grab it, those competent enough to have something of value to offer for sale; the clueless 95% will suffer, but that is only just. With crypto anarchy we can painlessly, without initiation of aggression, dispose of the nonproductive, the halt and the lame. (May, 1994b, 6.7.3)
This view was not universal among the cypherpunks, Assange argued:
the 95 percent of the population which compromise the flock have never been my target and neither should they be yours. It’s the 2.5 percent at either end of the normal that I have in my sights. (Bartlett, 2016)
This viewpoint represented a fundamental split within the cypherpunks. One segment, intellectually elite, productive and prosperous, resented the burden of the masses – they wanted to isolate themselves from these cerebral heathens, for why should they pay a government to subsidise the 95% when they receive nothing but oppression in return? The other segment, in which Assange resided, desired to focus its wrath on the overbearing government more than the citizens who gave its leaders power.
Beltramini argues the, “The key question at the heart of the cypherpunk movement was not freedom, but the crisis of freedom in a situation of extensive social control of dominant institutions over private individuals” (2020, p. 3). Further, Beltramini posits, “cypherpunks believed that technology, rather than law, can protect their freedom, not because the democratic system is wrong, but because it is broken” (2020, pp. 15–16). Whilst the cypherpunks believed the democratic system was broken, there is little evidence to support Beltramini’s implication that the cypherpunk’s objection to democracy was due to its current state of implementation, rather than due to the underling political philosophy. For instance, Perry Metzger posted in March 1993 that, “If history has had any lesson, it is that governments degenerate and are taken over by evil men, over and over and over” (Metzger, 1993). Further, it is unclear to what degree those branding themselves as anarchists were familiar with the philosophical underpinnings of that ideology, or whether their perceptions of anarchism were based on an idiosyncratic interpretation of anarchism. For instance, the crypto-anarchist manifesto makes no reference to philosophers which inspired the concept. However, one should keep in mind the mail list was only one point of congress for the cypherpunks, it is possible that the philosophy was further explored during physical meetings of the cypherpunks. The lack of sampled cypherpunks who branded themselves as anarchists reveals that this ideology was not wholly embraced by their community. For example, Phil Karn would post in November 1992 that he found himself a, “little uncomfortable with some of the more anarchist ideas expounded,” he was not, “interested in overthrowing the government by force,” but wanted to protect his privacy from everyone, especially the government, Karn believed, “good fences make good neighbours,” and, “good cryptography will make for good government.” Even May, in a rare moderate moment commented:
Overthrowing the government may not be such a hot idea […] the replacement could be much worse. But finding ways to preserve personal liberty is a good goal. Finding ways to selectively bypass the State is also a good goal. (May, 1994d)
The cypherpunks may have disagreed on the degree to which the State needed to be curtailed, but it seems almost their universal belief that government must be downsized, at the absolute minimum, into the smallest corner of public life. The hacker ethic the cypherpunks inherited proclaimed central authorities were to be distrusted, this imperative coloured the cypherpunk’s attitude in pursuing their goals of a technological check against the government.
The hacker ethic
“Hacking” culture first originated in 1959 at the Michigan Institute of Technology (MIT), where a hack was considered:
a project undertaken or a product built not solely to fulfil some constructive goal, but with some wild pleasure taken in mere involvement […] to qualify as a hack, the feat must be imbued with innovation, style, and technical virtuosity. (Levy, 2010, Chapter 1)
Steven Levy captures the core hacker tenets:
- Access to computers – and anything that might teach you something about the way the world works – should be unlimited and total.
- Always yield to the Hands-On Imperative!
- All information should be free
- Mistrust authority; promote decentralisation
- Hackers should be judged by their hacking, not bogus criteria such as degrees, age, race or position
- You can create art and beauty on a computer
- Computers can change your life for the better (2010, Chapter 2)
The most famous cypherpunk first-generation hacker was John Draper, alias “Captain Crunch.” For the cypherpunks, Draper’s presence was an important continuation of their intellectual and cultural hacker heritage (Rhoads, 2007). Hal Finney comments Draper was an, “inspiration to me when I was in college in the 1970s […] he represented […] the spirit of questioning authority and exploring beyond the accepted bounds of the system” (1992).
Another insight into the Hacker ethic is the Hacker Manifesto, also known as The Conscious of a Hacker (1994). The Manifesto is written by Loyd Blakenship, who went by the hacker alias “The Mentor,” and was a member hacker collective Legion of Doom. Blakenship, whilst being an early subscriber to the mail list he unsubscribed in early 1994 due to the volume of flaming (Blakenship, 1994. Blakenship wrote the Manifesto shortly after his 1986 arrest by the FBI for computer-related crimes. It was a time when hackers were being negatively portrayed by the press, especially following the WarGames movie that depicted a hacker inadvertently shepherding the world to the brink of nuclear apocalypse. The manifesto draws together a number of characteristics and views common amongst the hacker fraternity, Blakenship wrote, “I’m smarter than most of the other kids, this crap they teach us bores me […] we’ve been spoon-fed baby food at school when we hungered for steak.” Then he talks of finding technology for the first time:
I made a discovery today. I found a computer. Wait a second, this is
cool. It does what I want it to. If it makes a mistake, it’s because I
screwed it up. Not because it doesn’t like me…
Or feels threatened by me…
Or thinks I’m a smart ass…
And then it happened… a door opened to a world…rushing through
the phone line like heroin through an addict’s veins, an electronic pulse is
sent out, a refuge from the day-to-day incompetencies is sought…a board is
found.
“This is it…this is where I belong…”
I know everyone here…even if I’ve never met them, never talked to
them, may never hear from them again…I know you all. [9]
Ostracism from society is often felt by hackers. The Internet is a haven where one can discover like-minded peers from around the world. Judgements are based not on a physical manifestation of a physical form beyond their control, but on the authentic representation of their cultivated intellect – such an environment hackers migrate to and colonise:
This is our world now…the world of the electron and the switch, the
beauty of the baud. We make use of a service already existing without paying
for what could be dirt-cheap if it wasn’t run by profiteering gluttons, and
you call us criminals. We explore…and you call us criminals. We seek
after knowledge…and you call us criminals. We exist without skin color,
without nationality, without religious bias…and you call us criminals.
You build atomic bombs, you wage wars, you murder, cheat, and lie to us
and try to make us believe it’s for our own good, yet we’re the criminals.
Yes, I am a criminal. My crime is that of curiosity. My crime is
that of judging people by what they say and think, not what they look like.
My crime is that of outsmarting you, something that you will never forgive me
for. [10]
It was rare during the earliest days of hacking that coders would discuss the political or social implications of the technology they were developing. Hackers were seldom trying to instigate social change, theirs was a quest of the mind and heart, but for most hackers, it was not buttressed by a political ideological. But when the anti-authority hacker culture migrated to the west coast it became influenced by the counterculture and those desperate to find ways to resist the perceived government oppression (Levy, 2010).
One of the best reflections of the hacker and Cypherpunk philosophy is found in John Perry Barlow’s (1996) Declaration of the Independence of Cyberspace. Barlow posted occasionally to the cypherpunk mail list. Barlow’s declaration first of all seeks to undermine any authority Nation states claim in Cyberspace:
Governments of the Industrial World, you weary giants of flesh and steel, I come from Cyberspace, the new home of Mind. On behalf of the future, I ask you of the past to leave us alone. You are not welcome among us. You have no sovereignty where we gather.
Barlow continues to invoke liberty as the foundation of Cyberspace:
We have no elected government, nor are we likely to have one, so I address you with no greater authority than that with which liberty itself always speaks. I declare the global social space we are building to be naturally independent of the tyrannies you seek to impose on us. You have no moral right to rule us nor do you possess any methods of enforcement we have true reason to fear.
Barlow argues Cyberspace is a zone beyond that of the physical:
Governments derive their just powers from the consent of the governed. You have neither solicited nor received ours. We did not invite you. You do not know us, nor do you know our world. Cyberspace does not lie within your borders.
Barlow argues Cyberspace is self-governing, and governments do not understand how the digital world functions:
You do not know our culture, our ethics, or the unwritten codes that already provide our society more order than could be obtained by any of your impositions. You claim there are problems among us that you need to solve. You use this claim as an excuse to invade our precincts. Many of these problems don’t exist. Where there are real conflicts, where there are wrongs, we will identify them and address them by our means. We are forming our own Social Contract.
Barlow invokes the equality of digital citizens, that Cyberspace holds no biases, “We are creating a world that all may enter without privilege or prejudice accorded by race, economic power, military force, or station of birth.” The Declaration denounces the tyranny of the majority, “we are creating a world where anyone, anywhere may express his or her beliefs, no matter how singular, without fear of being coerced into silence or conformity.” Barlow claims the Internet’s inhabitants as part of another group of society that governments cannot understand, “You are terrified of your own children, since they are natives in a world where you will always be immigrants.” It was this sense of otherness causing Barlow to proclaim, “our virtual selves immune to your sovereignty, even as we continue to consent to your rule over our bodies. We will spread ourselves across the planet so that no one can arrest our thoughts.” Barlow intended the intended to be, “a civilization of the Mind,” and hoped, “it be more humane and fair than the world your governments have made before.” But the Cypherpunks did not merely want to create a new domain for the mind, their actions were fully intended to have impacts in the physical world, and to upend the status quo. [11]
The counterculture
Protest culture, and the associated counter-culture, ran deep within the cypherpunk community. Peter Wayner acknowledged the cypherpunks liked to, “cloak itself in the romance of the counter culture” (1993). Zimmermann illustrates this disposition – he was arrested several times for protesting nuclear testing along with arguably the most notorious whistle blower of all times, Daniel Ellsberg (Zimmermann, n.d.). Zimmermann became involved in nuclear protest at the start of the 1980s when he contemplated fleeing America (Zimmermann, n.d.). Zimmermann’s first son had just been born into a world where, in his words, “millions of people feared the world was drifting inexorably toward nuclear war” (Zimmermann, n.d.). Moving to the nuclear-free New Zealand seemed a wise decision to protect his young family, “We thought it would be a hard life in New Zealand after a war, but we thought it might still be liveable” (Garfinkel, 1995, p. 87). As Zimmermann and his wife were preparing their immigration papers in 1982, they were told of a conference taking place in Denver by a group called the Nuclear Weapons Freeze Campaign (Garfinkel, 1995, p. 87). It was in Denver, Zimmermann first heard Ellsberg speak. Zimmermann found the conference, “sobering but empowering” (Garfinkel, 1995], p. 87; Greenberg, 2012, Chapter 2). Ellsberg’s speech gave him hope, Zimmermann reflects, “It seemed plausible that this was a political movement that had some chance of success, of turning things around […] we decided to stay and fight” (Garfinkel, 1995, p. 87; Greenberg, 2012, Chapter 2). Zimmermann’s fight would ultimately manifest is his creation of the Pretty Good Privacy (PGP) encryption software which he gave away for free in 1991 providing a significant challenge to government surveillance.
“Counterculture” was first termed by Theodore Roszak in 1969. Roszak described the counterculture as, “a culture so radically disaffiliated from the mainstream assumptions of our society that it scarcely looks to many as a culture at all, but takes on the alarming appearance of a barbaric intrusion” (Roszak, 1969). The reason for this disaffiliation was routed in the events of world war two, when the age of atomic warfare dawned with a blinding flash above Hiroshima, causing 100,000 deaths (Zinn, 1980, p. 422). President Roosevelt directed some of the greatest scientific minds of his generation to build “the bomb”; Roszak believed the post-atomic youth were in rebellion at this inherited reality, as was Zimmermann (Roszak, 1969, p. 47). The Soviet Union achieved the bomb in 1949, the same year Chinese communists were victorious in their civil war. Stewart Brand, the organiser of the first hacker’s conference, recalls how the youth of the 1950s and 60 s felt, “we were the ‘now generation’ because we figured there would be no then. We were completely apoplectic, the sky was falling” (Turner, 2006, Chapter 4). May referred to Roszak’s work on the mail list, describing it as “influential” (May, 1995).
Technology was embraced by those of the counterculture. In particular, the Cybernetic theory of Norbert Weiner was seen as a model of how systems could be built in peer-to-peer, rather than hierarchical structures, this view echoed the anarchist and decentralised political structure that many of those in the counterculture coveted (Turner, 2006, Chapter 1). Technology was heavily utilised within the San Francisco “Trips festivals,” whose attendees were instructed to, “wear ecstatic dress and bring their own gadgets” (Turner, 2006, Chapter 1). These hedonistic gatherings fused together drugs, multimedia light shows, music and technology allowing revellers to experience new forms of consciousness during their trips. Many in the counterculture, believed that a techno-social society could be cultivated, where machines served humans and in turn humans served machines (Turner, 2006, Chapter 1). This sentiment was articulated by Richard Brautigan in his 1967 poem Machines of Loving Grace, “I like to think […] of a cybernetic ecology […] where we are free of our labors […] and all watched over by machines of loving grace.”
Science fiction: literature & film
Culture, especially cyberpunk literature and movies, played a significant role in articulating the narrative of the cypherpunk’s struggles and ambitions, Rid comments, “fiction stoked the cypherpunk movement’s utopian ideas” (Rid, 2016, Chapter 7). On some occasions, veteran dystopian novels, such as George Orwell’s 1984 were lauded as vivid portrayals of the possible future enabled by the assent of technology and its conscription by the powerful (May, 1994c). Throughout their early communications 1984 references were made, such as when Draper asked whether the “thought police” would burst down his door should he use PGP (1992). At other times the cypherpunks added contemporary reflections of their philosophy, such as the Sneakers movie, to their reference materials. “Read the sources,” May would insist, and top of the sources list was True Names (May, 1994b, 2.4.2).
Vinge’s (1981) True Names was one of the first novels to portray a granular depiction of cyberspace, it was one of the early sources to inspire the conception of crypto anarchy and held high status within cypherpunks lore, even being used as the basis for their discussions and conceptions on anonymity (Hughes, 1994). Hughes comments, “Many of us have been influenced by the fiction of Vernor Vinge, particularly his ‘True Names’” (Hughes, 1993b). True Names follows the journey of a hacker known as Mr. Slippery, whose true name was, “his most valued possession but also the greatest threat to his continued good health” (Vinge, 1981, p. 185). A hacker’s true name was their real-world identity. Hackers were powerful and evasive in cyberspace where only the mind can grant power, but in the flesh, they could be coerced or killed by the State. Daniel Ray articulated the asymmetric nature of the physical world and threat of governments that Vinge portrayed in True Names on the mailing list in early 1993:
Once it gets to a face-to-face confrontation, however, you lose, and you lose immediately, there is nothing you can bring to bear, since it is now just a force equation, and they have over 10,000 times the force you do.
As the story proceeds a mysterious hacker, the Mailman, emerges and wages war in an attempt conquer cyberspace. Mr Slippery and his ally Ery combine forces to stop the Mailman’s war, which risks spilling into the physical realm and devastating the world. Slippery and Ery are able to gather enough processing power to topple the Mailman, who is revealed as a rogue NSA artificial intelligence. Slippery and Ery acquire enough power to rule both the virtual and physical worlds, but after a brief contemplation, they “self-lobotomise” and relinquish their power, knowing that in order to preserve such power they would have to induce such suffering as to, “end up being worse than the human-based government” (Vinge, 1981, p. 242). Both hackers make this sacrifice despite being cognisant the government, which has identified their true names, will likely kill them when they relinquish their strength.
Orson Scott Card’s Ender’s Game of 1985 was also highly regarded by the cypherpunks (Dinkelacker, 1993). The subplot features two young, but exceptionally intelligent, children who cultivate online pseudonyms, or “nyms,” and eventually translate their online influence into real world political power. The ability to be represented solely by their thoughts, rather than their physical manifestation was a hacker ideal echoed by the author’s narrative:
With false names, on the right nets, they could be anybody. Old men, middle-aged women, anybody, as long as they were careful about the way they wrote. All that anyone would see were their words, their ideas. (Card, 1985, p. 134)
Finney reflected on the societal vision expounded by Ender’s Game notion of anonymity:
[users] can make unpopular arguments or participate in frowned-upon transactions without their activities being linked to their true identities. It also allows people to develop reputations based on the quality of their ideas, rather than their job, wealth, age, or status. (Finney, 1993)
Many of the cypherpunks already possessed the societal respect they craved, being highly educated and often leaders in their respective fields. It was likely the anonymity provided by pseudonyms was more valuable as a means of a stable presence in cyberspace divorced from their true names. This further allowed them to protect their true lives from a government they perceived as armed and dangerous. Ender’s Game also features a war-hungry government that manipulates a young, talented child into leading a military operation resulting in their committing genocide against an alien species, this conformed well to the cypherpunk’s perception of authority.
The translation of cyberspace effects in the real world was well portrayed by another cypherpunk favourite, John Brunner’s 1975 novel, The Shockwave Rider. The protagonist, Nickie Haflinger, makes use of a society endowed with ubiquitous computing to evade the authorities hunting him. Haflinger uses the extensive computing training he received at a secret government facility to break into secure networks and create new identities for himself as required. After Haflinger creates a worm designed to leak all government data online, the government launches nuclear weapons against him, Haflinger uses his technical and social-engineering skills to stop the inbound missiles before they reach him, thus enacting what would later become a cypherpunk dream – the neutralisation of the government’s monopoly on violence. The Shockwave Rider is also notable for the prevalence of digital payments having mostly replaced cash, allowing the government to monitor how each of their citizens were spending their earnings; a cypherpunk nightmare. May comments, “in many ways it [Shockwave Rider] prepared me for my later role as a hunted CyberFelon” (May, 1994d).
Tyrannical Governments. Anonymity and pseudonymity. Dystopian Futures. Imminent apocalypse. Ubiquitous technology and connectivity. These themes permeate the literary outputs that form the cypherpunk’s cannon, and what could manifest should their ambitions fail. The other constant in the cypherpunks literary inspirations was a downtrodden hero, often cast aside by kin, disregarded by society, and exploited by government. In cyberspace they believed the champion could have outsized abilities to right the perceived wrongs visited upon themselves and society, and in the process, save the world.
Conclusion
This article has argued that the cypherpunks were a highly educated, primarily libertarian community permeated by aspects of anarchism which arose from their societal disaffiliation inherited from the counterculture. Further, this article has argued that the cypherpunks objectives were directed to minimise, or even remove the State from public life, and that they were heavily influenced by the hacker ethic and dystopian science fiction.
This adds to our understanding of the cypherpunks as a community. However, we still lack a thorough understanding of how successful their actions were in fomenting the wider encryption-technologies for which they advocated, such as anonymity networks and crypto currencies. Further study should also be conducted to understanding how prevalent their thinking remains today within the technical community and broader society.
Declaration of interest statement
The author has no financial interests in this research.
Acknowledgments
The author would like to express his thanks to Professor Keith Martin for his comments on this article, and to Dr. Emmett Sullivan, for his earlier guidance. Additionally, the author thanks the two anonymous reviewers who offered insightful comments which further strengthen this article.
Notes on contributors
Craig Jarvis is an independent cyber security strategist completing a PhD in Information Security & History at Royal Holloway, University of London. Craig holds master’s degrees in Cyber Security, International Security, and Classical Music, and studied history at Oxford University. Craig’s first book, Crypto Wars – The Fight for Privacy in the Digital Age: A Political History of Digital Encryption, was published by CRC Press in December 2020.
Notes
-
For instance, in 2016 the FBI took Apple to court when they refused to unlock a terrorist suspect’s iPhone, the court ruled against the FBI (Orenstein, 2016).
-
For instance, see the “Cypherpunk Bitstream” podcast as an example of the modern cypherpunk community.
-
For instance, see: Froomkin (1995), Böhme et al. (2015), Bellia (2012), and Jarvis (2020).
-
The data set is complete with the exception of a gap between March and July 1995. An absence of commentary on this data gap within the mail list suggests it is likely caused by archival issues rather than a lack of activity.
-
Due to the use of anonymity technologies, and multiple email accounts, it is impossible to generate an accurate user count.
-
128-bit RC4.
-
Dumpster diving is the process of searching through someone’s trash in order to ascertain personal details about their lives, details that can often be used to facilitate subsequent action.
-
Original ellipsis and indentation.
-
Original ellipsis.
-
Further treatment of the hacker ethic is beyond the scope of this work, for additional information on the genesis of hacking see Levy’s seminal Hackers: Heroes of the Computer Revolution (2010).
-
Today we call this ‘astro-turfing,’ the suggestion of false grass-roots support or development for an idea.
References
-
Bartlett, J. (2016). Cypherpunks write code. American Scientist. Wayback Machine https://www.americanscientist.org/article/cypherpunks-write-code
-
Bell, J. (1997, April 3). Assassination Politics. Cryptome. Wayback Machine https://cryptome.org/ap.htm
-
Bellia, P. L. (2012). WikiLeaks and the institutional framework for national security disclosures. The Yale Law Journal, 121(6), 1448–1526.
-
Beltramini, E. (2020). Against Technocratic Authoritarianism: A short intellectual history of the cypherpunk movement. Internet Histories. https://doi.org/10.1080/24701475.2020.1731249
-
Bentham, J. (1843). The works of Jeremy Bentham, vol. 11 (Memoirs of Bentham Part II and Analytical Index). Online Library of Liberty. Wayback Machine The Works of Jeremy Bentham, vol. 11 (Memoirs of Bentham Part II and Analytical Index) | Online Library of Liberty
-
Boaz, D. (2015). The libertarian mind. Liberatianism.org. Wayback Machine https://www.libertarianism.org/guides/introduction-libertarianism
-
Böhme, R., Nicolas, C., Edelman, B., & Moore, T. (2015). Bitcoin: Economics, technology, and governance. Journal of Economic Perspectives, 29(2), 213–238. https://doi.org/10.1257/jep.29.2.213
-
Brautigan, R. (1967). All watched over by machines of loving grace. brautigan.net. https://web.archive.org/web/20070223021032/http://www.brautigan.net/machines.html
-
Card, O. S. (1985). Ender’s Game. Tor Books.
-
Chaum, D. (1985a). Security without identification: Transaction systems to make Big Brother obsolete. Communications of the ACM, 28(10), 1030–1044. Security without identification: transaction systems to make big brother obsolete | Communications of the ACM
-
Chaum, D. (1985b). Security without identification: card computers to make Big Brother obsolete. chaum. Wayback Machine Security without Identification - chaum.com.
-
Cypherpunk Bitstream Podcast. (2020). Cypherpunk bitstream podcast. Wayback Machine Cypherpunk Bitstream Podcast - TAZ 0
-
Dahlberg, L. (2010). Cyber-Libertarianism 2.0: A discourse theory/critical political economy examination. Cultural Politics: An International Journal, 6(3), 331–356. Cyber-Libertarianism 2.0: A Discourse Theory/Critical Political Economy Examination | Cultural Politics | Duke University Press
-
Dexheimer, E. (1993, September 29). Secret agents. Denver Westword, 12.
-
Froomkin, M. A. (1995). The metaphor is the key: Cryptography, the clipper chip, and the constitution. University of Pennsylvania Law Review, 143(3), 709–897. https://doi.org/10.2307/3312529
-
Garfinkel, S. (1995). PGP: Pretty Good Privacy. O’Reilly Media Inc.
-
Greenberg, A. (2012). This machine kills secrets: How wikileakers, cypherpunks, and hacktivists aim to free the world’s information. Random House.
-
Hospers, J. (1971). Libertarianism: A political philosophy for tomorrow. Nash Publishing.
-
Jarvis, C. (2020). Crypto wars: The fight for privacy in the digital age, a political history of digital encryption. CRC Press.
-
Lessig, L. (2006). Code 2.0. Basic Books.
-
Levy, S. (2010). Hackers: Heroes of the Computer Revolution – 25th anniversary edition. O’Reilly Media.
-
Martin, K. (2020). Cryptography: The key to digital security, how it works, and why it matters. W.W. Norton & Company.
-
Milhon, J. (n.d). The nerdgirl’s pillow book, or, the joy of hacker sex. Jude Milhon’s Webpage. https://web.archive.org/web/20070814112409/ AOL is part of the Yahoo family of brands
-
Orenstein, J. (2016, February 29). Memorandum and Order. United States District Court Easter District of New York. Wayback Machine https://cdn1.vox-cdn.com/uploads/chorus_asset/file/6124209/Orenstein-Order-Apple-iPhone-02292016.0.pdf
-
Palys, T. (2008). Purposive sampling. In L. M. Givens (Ed.), The Sage encyclopaedia of qualitative research methods (Vol 2, pp. 697–698). Sage Publications.
-
Rid, T. (2016). Rise of the machines: The lost history of Cybernetics. W. W. Norton & Company.
-
Rhoads, C. (2007, January 13). The twilight years of Cap’n Crunch. Wall Street Journal. https://web.archive.org/web/20210314162356/ https://www.wsj.com/articles/SB116863379291775523
-
Roszak, T. (1969). The making of a counter culture: Reflections on the technocratic society and its youthful opposition. Anchor Books.
-
Slater, D. (1997, March 14). Secret agents. Bay Area Weekly. https://web.archive.org/web/20110610153125/ http://groups.csail.mit.edu/mac/classes/6.805/articles/crypto/cypherpunks/bay-area-weekly-march-14-97
-
Turner, F. (2006). From counterculture to cyberculture: Stewart Brand, The Whole Earth Network, and the Rise of Digital Utopianism. University of Chicago Press.
-
United States Congress. (2020, March 5). S.3398 – EARN IT act of 2020. United States Congress. https://web.archive.org/web/20210305003937/ https://www.congress.gov/bill/116th-congress/senate-bill/3398/text
-
United States Library of Congress. (n.d.). Federalist papers: Primary documents in American history. United States Library of Congress. https://web.archive.org/web/20210313183739/Full Text of The Federalist Papers - Federalist Papers: Primary Documents in American History - Research Guides at Library of Congress
-
United States Senate. (2020). The lawful access to encrypted data act. United States Senate. Wayback Machine https://www.judiciary.senate.gov/imo/media/doc/S.4051%20Lawful%20Access%20to%20Encrypted%20Data%20Act.pdf.
-
Vasvari, R., & Scarselli, G. (1996). Plaintiff seeks summary judgment in Cleveland case challenging licensing of “exports” of cryptographic information. Case Western Reserve University. Retrieved June 3, 2020, from https://web.archive.org/web/20060912162151/ http://samsara.cwru.edu/comp_law/jvc/pressrel2.html
-
Vinge, V. (1981). True names. Dell Publishing.
-
Zimmermann, P. (n.d). The early roots of PGP. philzimmermann.com. Wayback Machine https://philzimmermann.com/EN/background/peace.html
-
Zinn, H. (1980). A people’s history of the United States. HarperCollins Publishers.