All content found at https://moneroinfodump.neocities.org/
c0mmando: I’m mirroring this valuable resource for archival purposes. Some dead links have been replaced with archived versions.
Support the creator of this work by donating XMR:
89pw9u2ZcUcHwWns3vzd9Ng2fi7FHEhbecKfSmtSxRAb7t9Wg4MMtoZJdgBzyFwm96Q1Gdrtp8uaVZDGz4ovvLtGEuFDKd2
Archives
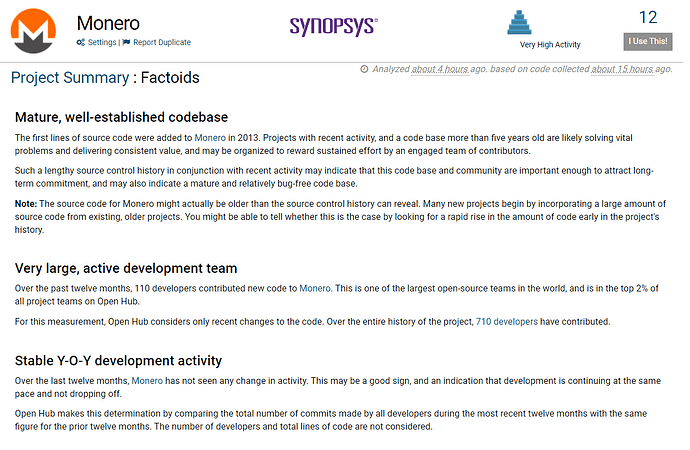
/XMR/ Monero General Info-Dump
#xmrgeneral:matrix.org
Monero Community Index
Monerica Business Directory
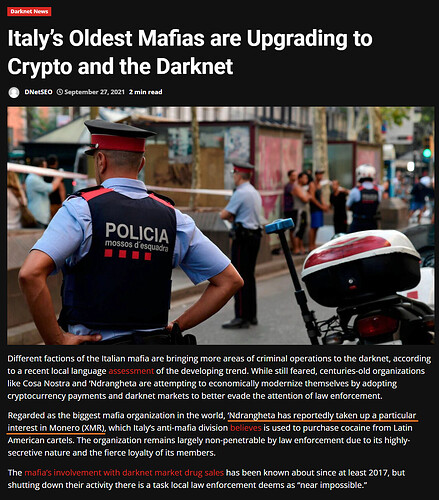
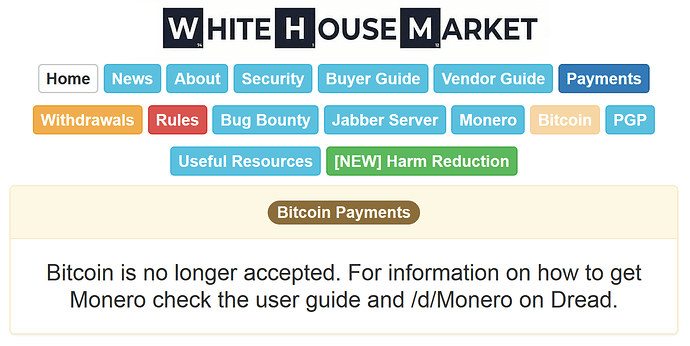
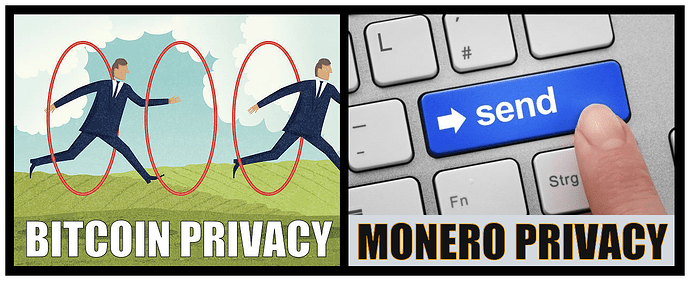
Monero: it’s what new Bitcoin users think they bought. Every feature, explained
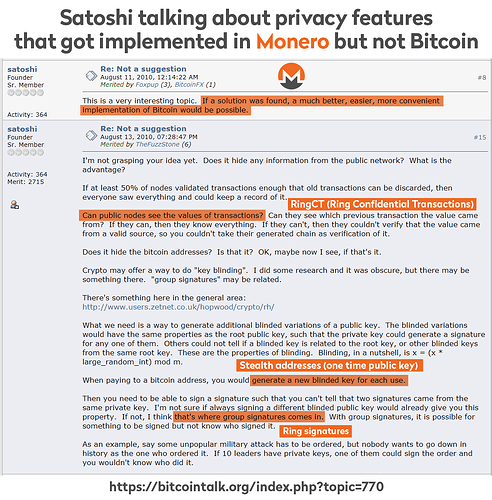
Monero is what Satoshi wanted Bitcoin to be
Required Viewing
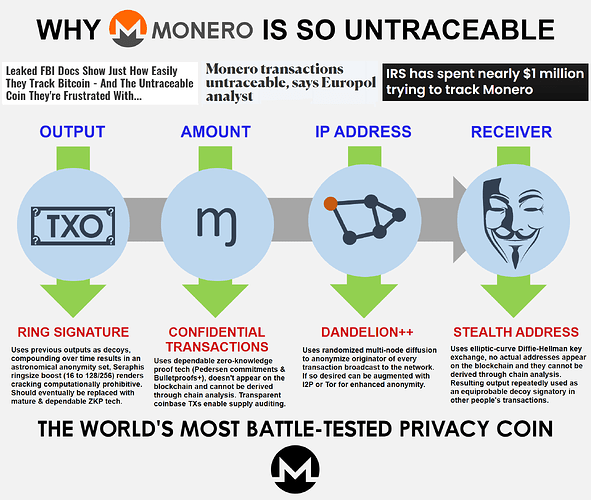
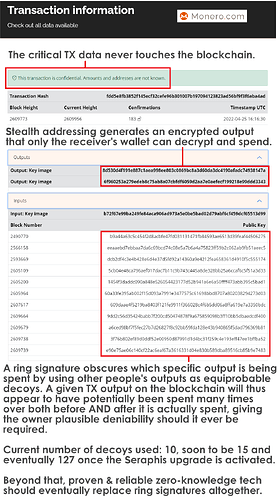
Why Monero is so untraceable
- nobody inspecting the blockchain can deterministically prove which output is being spent. (Ring Signatures)
- nobody inspecting the blockchain can determine the amount of XMR being transacted. (Confidential Transactions)
- nobody inspecting the blockchain can determine to whom the XMR was sent. (Stealth Addresses)
- Dandelion++ provides network-level shielding of IP addresses. I2P/Tor are also an option.
TL;DR: Monero addresses and amounts do not appear on the blockchain and thus cannot be derived through chain analysis.
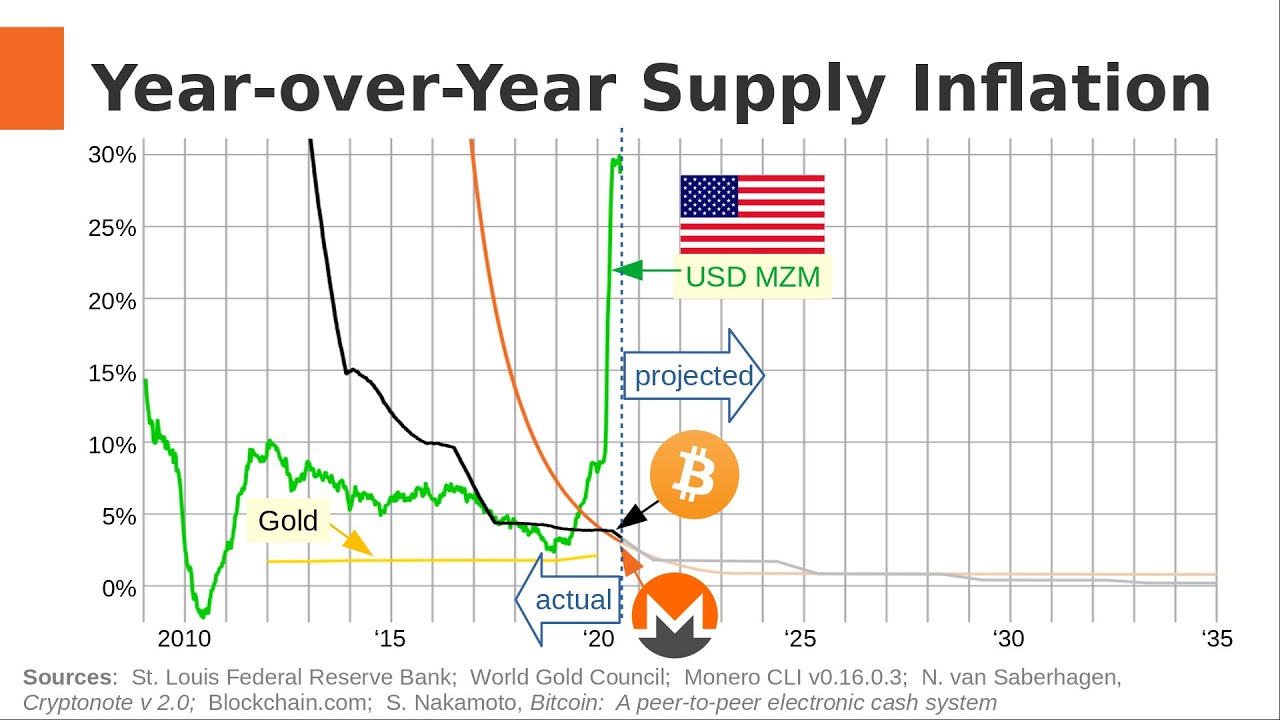
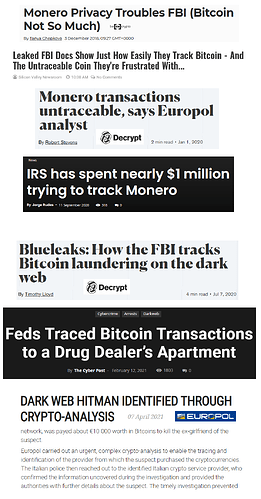
Monero’s all-round reliability can be evidenced by the fact that it has a 100% perfect track record, literally not a single real-world user has ever been traced despite repeated de-anonymization efforts by the likes of the FBI, Europol and the IRS, who are otherwise successfully tracing and prosecuting Bitcoin users on the darknet and elsewhere.
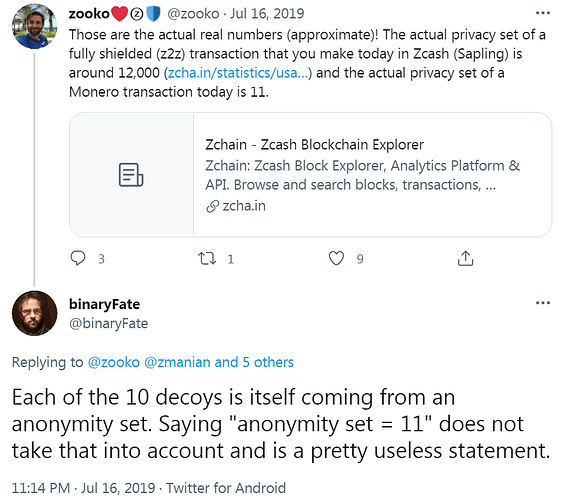
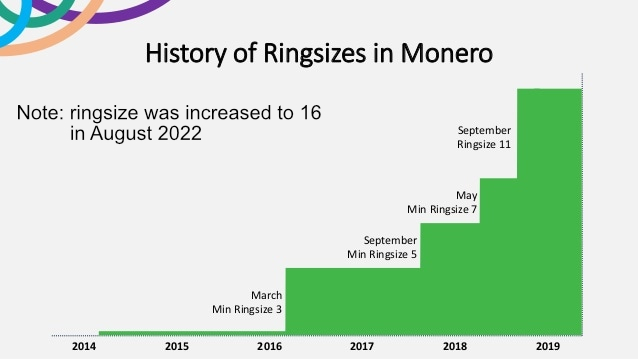
With regards to ringsize and anonymity sets, note that your personal anonymity set grows (compounds) over time even if you do nothing. This is how decoy inputs with ring signatures work, since a given output will continue to appear in different ring signatures in different blocks at different times its anonymity set grows infinitely.
So no, your effective anonymity set is definitely not just CURRENT_RINGSIZE, it pretty quickly grows to hundreds, thousands and hundreds of thousands of potential outputs on the chain. And once Triptych Seraphis increases the ringsize from 11 to 128, multiply all that by 12. GAME FUCKING OVER for anybody still trying to crack ring signatures.
Monero utilizes established, decades-old i.e. certifiably reliable cryptography and will in future integrate more comprehensive, currently experimental zero-knowledge solutions (zk-SNARKs/STARKs) once they mature and their trade-offs become less prohibitive. Research is ongoing.
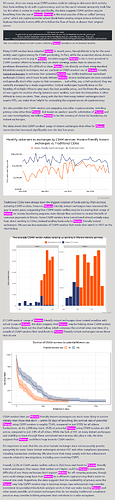
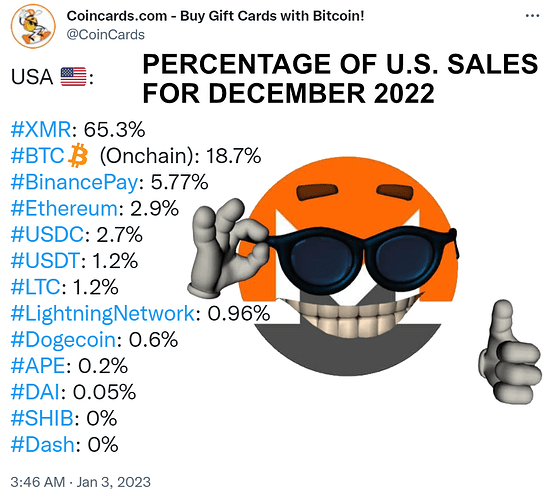
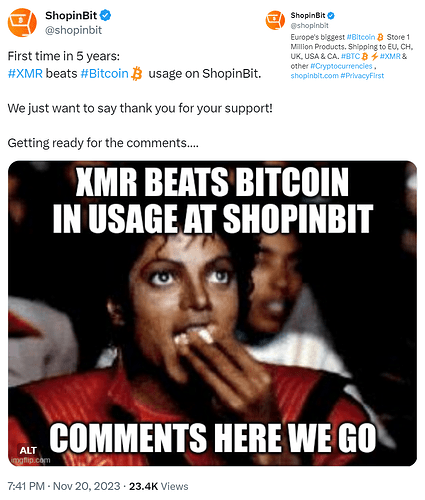
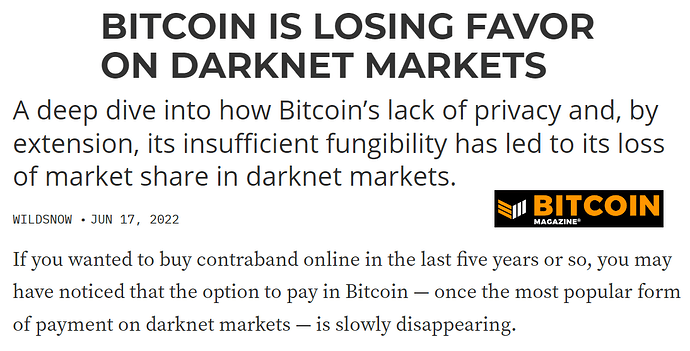
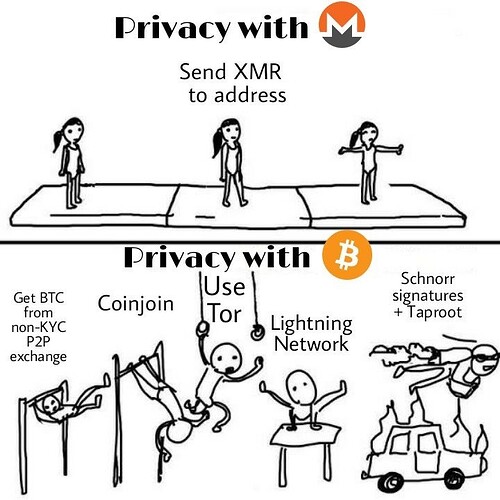
Monero is currently replacing Bitcoin wherever privacy & fungibility matter
Continuing advances in chain analysis have gradually eroded Bitcoin’s already tenuous fungibility to the point that it can no longer compete in markets where fungibility and privacy in particular are absolutely critical. This has inevitably resulted in a piecemeal exodus from Bitcoin into Monero, which, as the world’s most battle-tested privacy coin, is uniquely qualified to reliably service the transactional stealth requirements of an ever-growing number of cryptocurrency users.
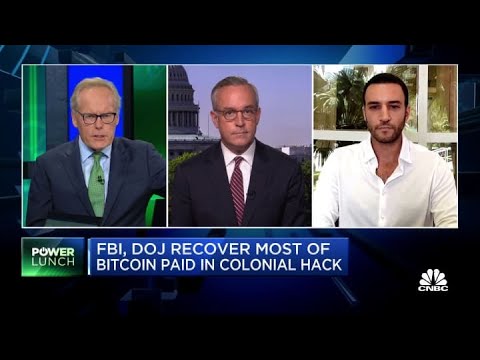
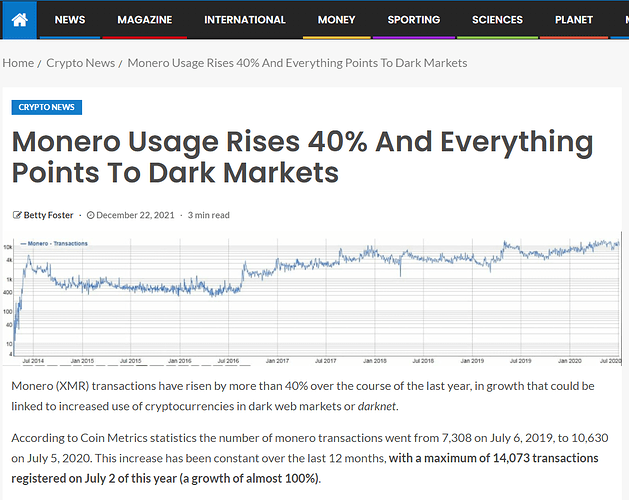
Monero’s surging adoption is now also being discussed on mainstream tv news reports.
Colonial Pipeline paid ransom to hacker group DarkSide
Bitcoin is the greatest thing to happen to the FBI: BlockTower’s Bucella
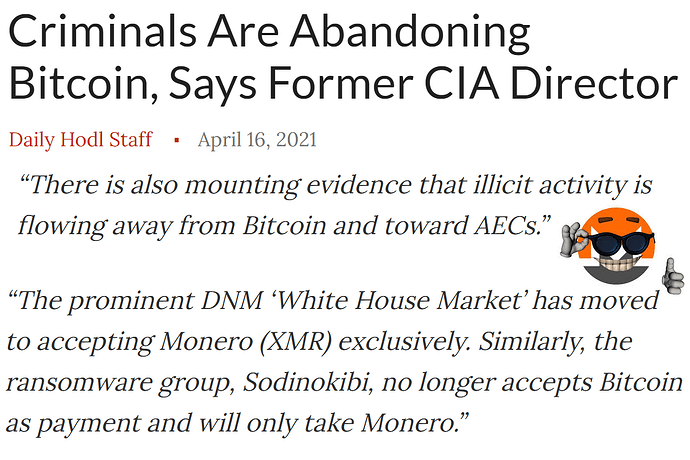
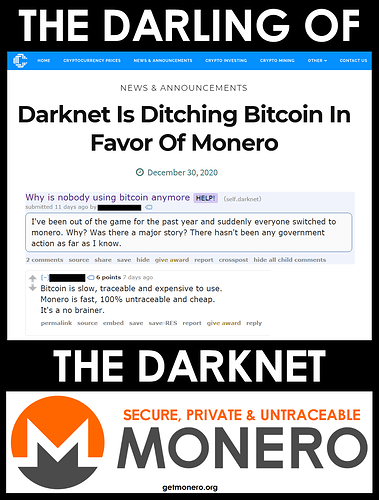
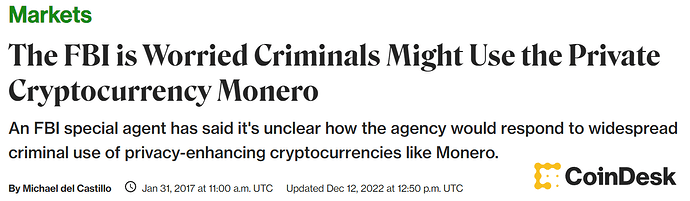
Why some hackers are ditching Bitcoin for a cryptocurrency called Monero
Last Week Tonight with John Oliver
BONUS: John McAfee’s legendary coke-fueled rant on XMR vs BTC
BONUS: Mental Outlaw - How Monero Works (And Why Its A Better Currency Than BTC)
BONUS: Mental Outlaw - Bitcoin is for Fools, Monero Rules!
BONUS: Coin Bureau - Monero: Why XMR Has So MUCH POTENTIAL!!
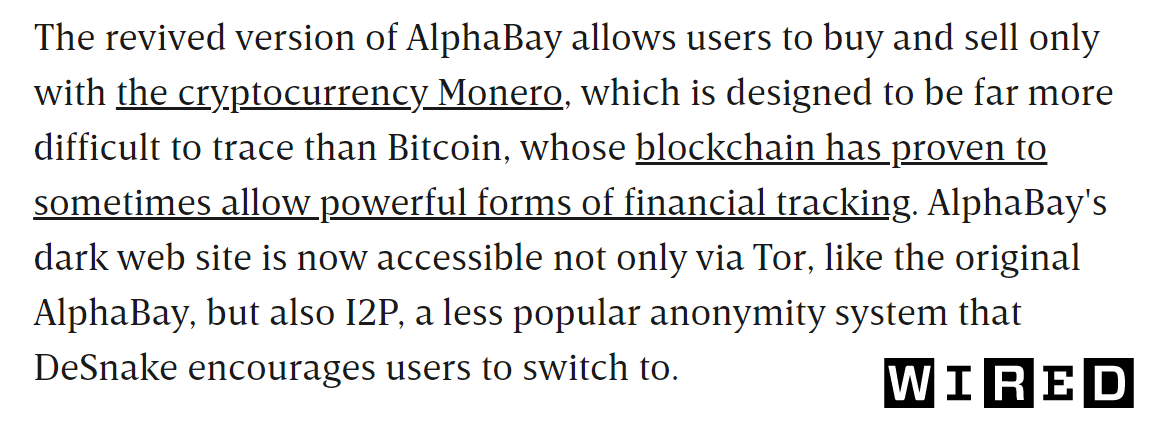
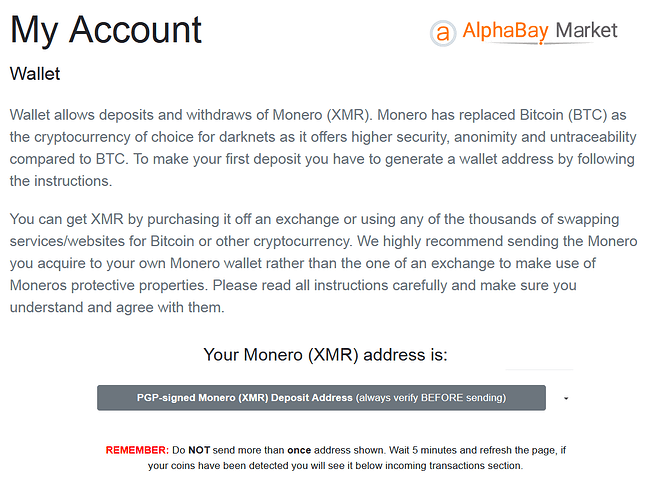
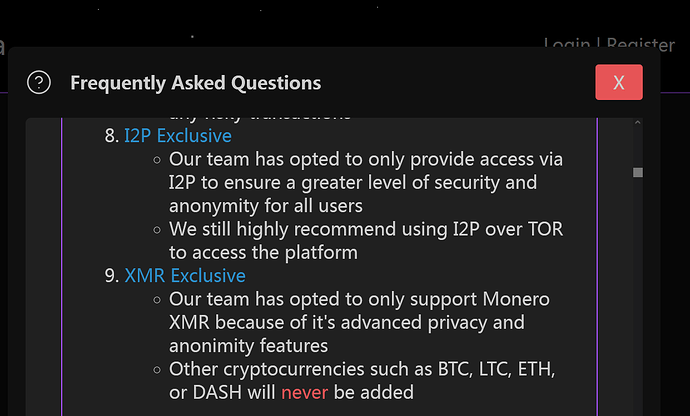
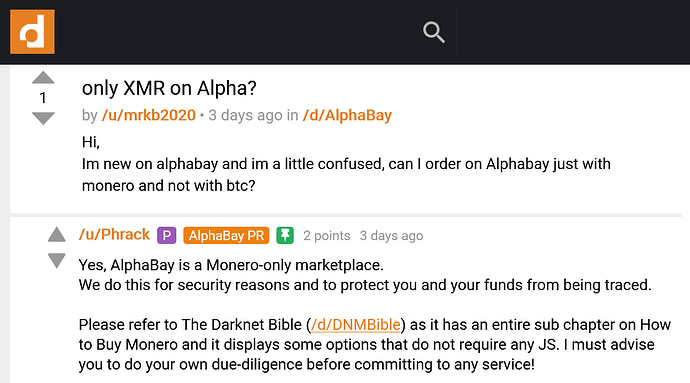
Dutch academic & DNM researcher: “Monero-only markets are the new standard.”
Recognizing traceability FUD
A common habit of FUDsters, particularly those shilling competing privacy projects, is to routinely allege that Monero is somehow broken or compromised, often while citing apparent research to that effect. While at first these claims and accompanying research might seem compelling, the fact that the Monero-using darknet and criminal underworld aren’t deterred by such allegations should be your first hint that you might be dealing with some good old fashioned bullshit.
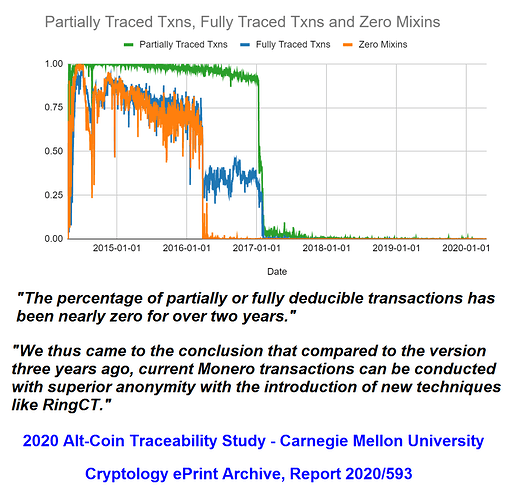
A typical FUD tactic involves citing outdated, pre-2018 data and hoping you won’t think to ask about it’s age. Namely, Monero is a constant work-in-progress that only keeps getting more and more secure with age, meaning it used to be somewhat less so a few years back when 0-decoy or non-fixed mixins were allowed and amounts weren’t yet shielded (pre-RingCT).
At that time, these vulnerabilities could be exploited to make deducing the true spend (ring member) much easier, though stealth addresses obviously remained unassailable so you still retained a respectable degree of privacy. Some studies were published that highlighted these potential issues and in due course the Monero devs upgraded and reinforced the protocol to the point that the prevalence of previous traceability issues is now effectively zero.
Another thing to watch out for are flawed or misleading studies that are based on theoretical exercises as opposed to real-world combat e.g. flood attack simulations:
In any case, a dedicated FUDster may also typically try to convince you that:
- Ring signatures are the linchpin of Monero’s privacy protocol and with them broken Monero would instantly become traceable.
- Ring signatures are broken because reasons.
The first one is wrong because ring signatures really only serve to provide plausible deniability about which output is being spent, the bulk of Monero’s privacy is actually provided by stealth addresses & CT, which shield the critical data i.e. addresses and amounts. Those remain off-chain and rock-solid. Furthermore, identifying the true spend doesn’t automatically translate into identifying the actual real-world user, without correlating KYC information there is literally nothing else to go on and this factor will become much more significant as zero-KYC DEXs like the upcoming Haveno start to gain traction.
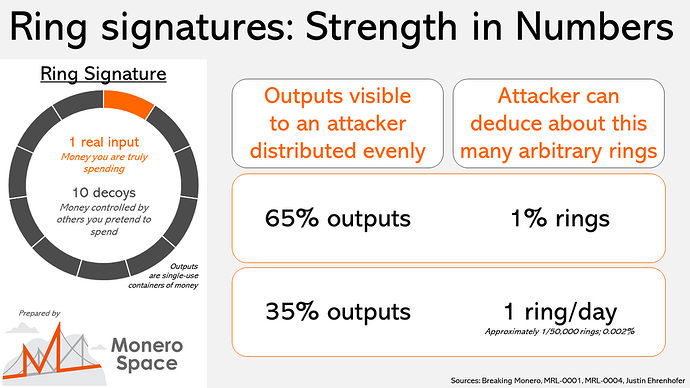
The second assertion fails to take into consideration how challenging it would actually be to meaningfully “break” ring signatures in an unpredictable real-world setting. To put things in perspective, despite the sheer volume of transactions involved an attacker would somehow have to maintain consistent and exclusive control over 65% of ALL outputs to compromise just 1% of arbitrary rings per day. Raising the ringsize from 11 to 20 would up that percentage to 80%.
So when you consider the fact that the upcoming Triptych Seraphis upgrade will enable ringsizes as large as 128, the utter futility of even trying to break ring signatures this way becomes glaringly obvious.
How the Seraphis upgrade will further enhance Monero’s capabilities
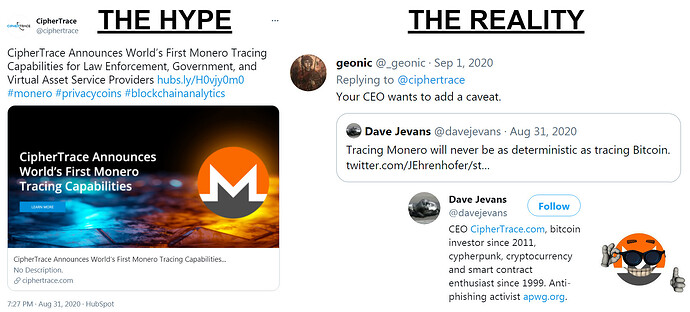
No, CipherTrace has obviously NOT cracked Monero
Literal fake news and vaporware. The primary red flag here is that CipherTrace is seemingly claiming to be able to do something that more reputable chain analysis enterprises openly concede is not likely to be feasible, namely tracing Monero transactions. Since Monero is an open source project with a well-understood privacy protocol it is exceedingly unlikely that CipherTrace has managed to discover some devastating new vulnerability that literally every other competitor and pen-tester have missed in their consistent, years-long efforts to crack Monero.
However, what is much more likely is that CipherTrace is simply trying to generate media hype in an effort to raise their profile, and nothing gets people’s attention like performing a miracle, in this case apparently cracking crypto’s esteemed king of privacy.
But the dead giveaway that CipherTrace is, to put it mildly, greatly exaggerating their Monero-tracing ability is:
- there has been no practical demonstration of their tech in action.
- the vague, sales pitch-laden and contradictory messaging they use.
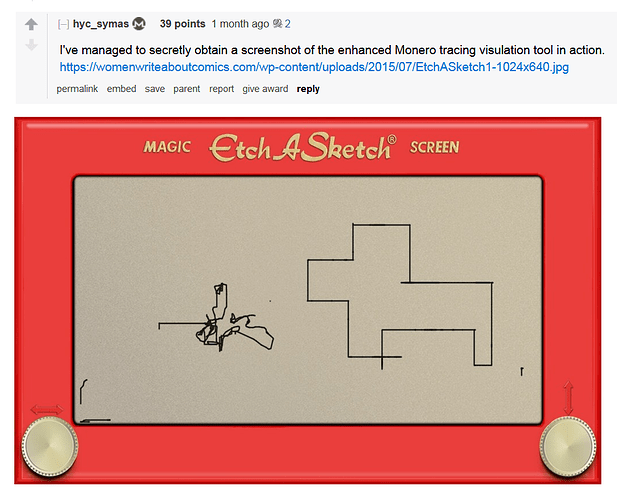
Apparently they haven’t so much developed a viable no-nonsense tracing protocol as they have fabricated a “next-generation enhanced Monero tracing visualization tool” that somehow manages to work despite the CEO already having acknowledged that they can’t actually trace Monero deterministically. It seems the whole thing is ultimately just a glorified probabilistic guessing game where CipherTrace spams the network with transactions in a Hail Mary attempt to filter out and guesstimate the likely true ring members i.e. outputs, followed by correlating what little they’ve got with available KYC data in the hopes of making a connection to an actual real-world identity.
In other words, as long as you’re practising basic, common-sense OPSEC i.e. ensuring your shady dealings are more than one TX removed from any subsequent KYC deposit, not spending funds immediately after receiving them, using subaddresses or fresh accounts, etc then the already low likelihood of your output being pegged as the true spend goes down to effectively zero. It bears reminding that Monero addresses and amounts DO NOT APPEAR ON THE BLOCKCHAIN so even if CipherTrace (or anybody else for that matter) somehow, against all the odds managed to identify your output that still wouldn’t reveal anything about how much XMR was actually sent and to whom, your plausible deniability would thus still remain viable.
Of course, you might be wondering: what is the point of developing and marketing a Monero tracing tool that doesn’t actually work? The answer is simple: it’s all compliance theater and CipherTrace’s tool is merely a prop to be used accordingly. In their own press release they state:
“The availability of this enhanced Monero tracing bolsters the viability of privacy coins for the long-term, assuring regulators that exchanges, OTC desks, and other virtual asset service providers will be able to comply with global Anti-Money Laundering requirements while continuing to accept Monero transactions.”
Pricing for source tracing of Monero transaction capabilities starts at $16,000 USD per year, per user, for existing licensed CipherTrace users at selected customers and agencies.
So if you’re an exchange and you want to make or keep Monero available to your customers you now need to be demonstrably proactive with regards to AML regulations and such and for the small sum of $16K per year CipherTrace can cover your ass and verify that you did indeed do everything you were supposed to, up to and including “monitoring” suspicious Monero transactions. Yeah, it didn’t amount to anything but at least you tried, right? It’s actually win-win for everybody involved: CipherTrace gets paid, the exchange is certified as compliant and Monero keeps being available to customers.
And in the end it turns out that CipherTrace’s little publicity stunt most definitely did not backfire on them: in early September 2021 it was revealed that MasterCard will be acquiring CipherTrace for an unknown amount (kek) of USD. Well played, gentlemen!
Vaporware: How to Spot Bogus Claims
CipherTrace’s Monero Tracking Tool Has Not Been Proven Effective, Researcher Says
Watch CipherTrace CEO struggling to convince amused MoneroChads that he has a magic crystal ball
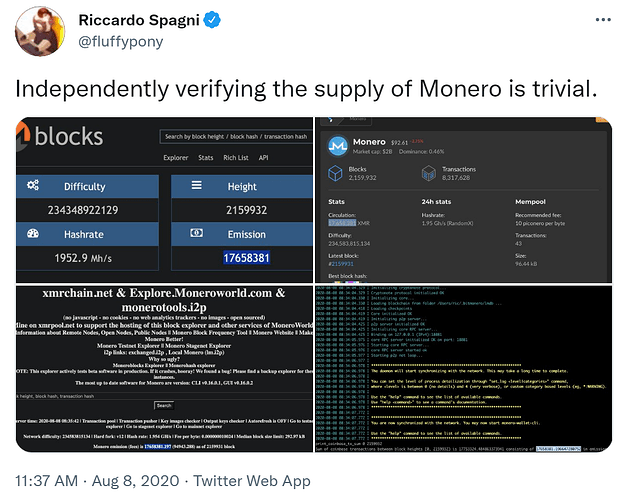
Yes, you can actually verify the XMR supply
Muh inflation bug" is some of the more common Monero FUD one will encounter on /biz/ and elsewhere, essentially the implication here is that because amounts are fully shielded, because we can’t directly observe and tally them up like we can with Bitcoin that there is then no way of knowing what’s really going on under the hood and that therefore all manner of inflationary fuckery might be happening without it being obvious. The most prevalent FUD narrative is that the devs have secretly been exploiting this bug for all these years, minting millions of extra XMR thus keeping the price so inexplicably low…
To understand why such theories are bullshit, we first need to establish one very relevant fact: prior to the introduction of RingCT in January 2017 XMR amounts were NOT SHIELDED, meaning that while user identities remained unknown the specific amounts they were transacting were on public display for everybody to see. Obviously this would then make any profiteering from an active inflation bug impossible to hide, millions of excess XMR moving around and getting dumped on exchanges would have immediately been noticed.
So we can therefore be quite confident that up until the activation of RingCT no meaningful inflation bug was active or being exploited. There was however a dormant inflation bug discovered earlier that same year, a relic of the original Bytecoin code Monero forked off from. Subsequent audits showed that the bug was NOT exploited, as was already obvious, and the offending code was patched.
Thus, when talking about “muh inflation bug” only the RingCT-era, 2017-present day, is relevant. And this is where one can legitimately pose the question: how can we be confident that millions of excess XMR aren’t being minted right now?
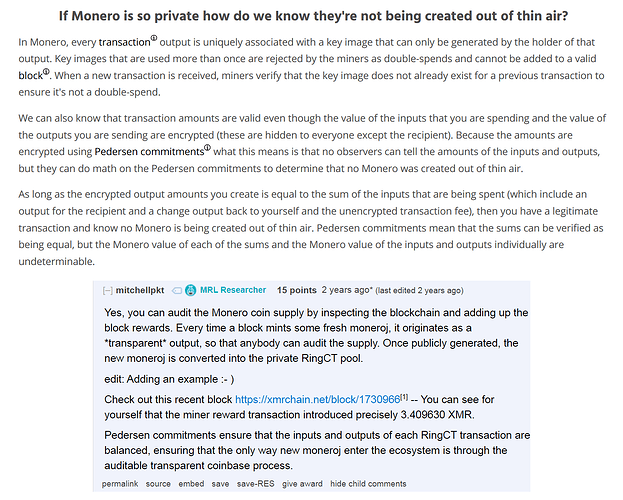
Namely, within RingCT XMR amounts are set and encrypted using a zero-knowledge proving system, specifically Pedersen commitments. The resulting homomorphic hash can then have mathematical calculations performed on it to verify the validity of its hidden value. In other words, even without knowing, without being able to directly observe specific XMR amounts we can still nonetheless mathematically prove their correctness and confirm that no extra coins have materialized i.e. that inputs and outputs are balanced and everything adds up perfectly, ergo “zero-knowledge” proof.
But how can we be so certain that these Pedersen commitments actually do what they’re supposed to? Well, the most significant reason is that unlike more novel ZKP variants, Pedersen commitments are an established, decades-old scheme, having debuted in 1991. That means they have 30 years of continuous use and battle-testing under their belt, we know how they work and, crucially, that they work, which thus makes them very predictable and therefore highly reliable.
As far as their implementation in Monero’s codebase goes, RingCT was obviously subjected to intense stress-testing and underwent several rounds of 3rd-party auditing before finally being activated to ensure everything is working optimally.
But the most practical way to validate the opaque accounting is by summing up block rewards i.e. coinbase outputs. Since freshly-minted coins have no transaction history, they don’t require shielding, meaning every single XMR coin that enters the ecosystem is briefly visible until it forever disappears into the shielded RingCT pool. Because the fixed emission rate tells us exactly how many coins should be in circulation at any given moment, as long as the tally of coins transparently entering the ecosystem = the expected in-circulation number we can be very confident that the underlying math keeping everything in check is working properly.
Furthermore, double-spending of existing amounts is prevented by key images. A key image is unique to each output and is only revealed once the funds have been spent. This allows anybody to verify that the amount to be spent hasn’t already been transacted before.
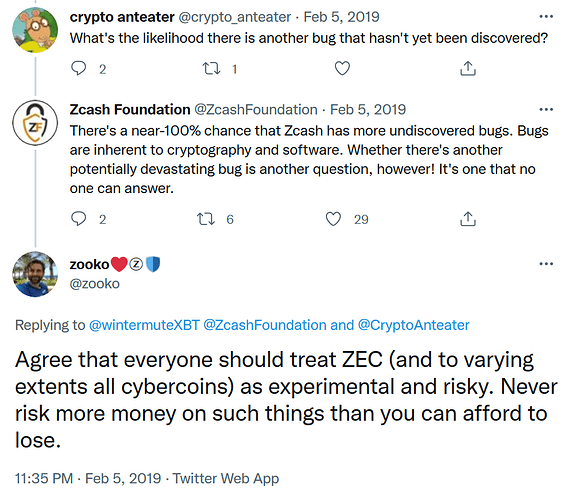
Now, there are obviously no 100% guarantees when it comes to software of any kind, including highly eyeballed code like Bitcoin, which has technically had twice as many inflation bugs as Monero:
- 2010: bug was exploited with 184 billion BTC being minted
- 2018: bug was not exploited but had gone undetected for 2 years
The lesson here being that undiscovered bugs are always a possibility but at some point you just have to accept that the code has been sufficiently audited and battle-tested and move on. It’s why you don’t ponder the validity of the underlying code every time you generate a new Bitcoin address, you simply have faith that everything is working properly even though there is a non-zero chance that a bug in the system is producing faulty private keys which may be compromised in future. Ultimately, the more time that passes without such a bug being detected the more confident we can be that it doesn’t exist and eventually we just stop worrying about it.
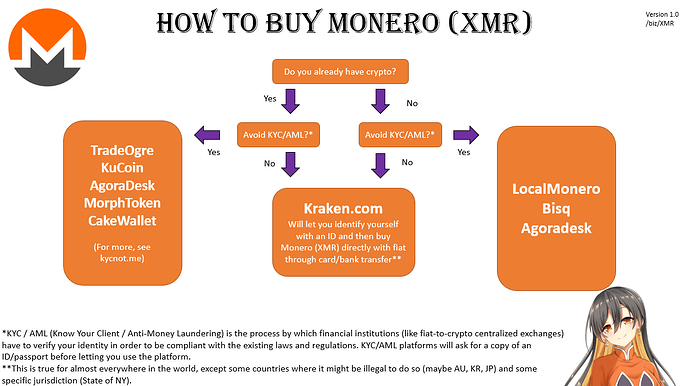
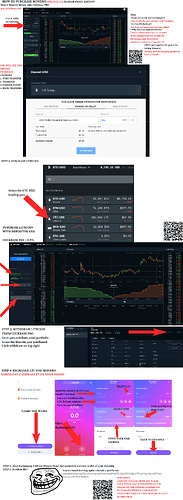
How to buy & store Monero
How to buy Monero for burgers
How to create a Monero paper wallet
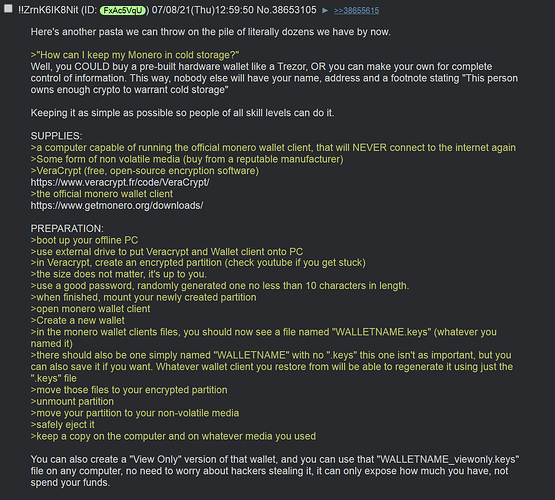
How to move Monero into cold storage
How BTC<->XMR atomic swaps will work under the hood
https://www.monerooutreach.org/stories/monero-atomic-swaps.html
COMING SOON: Haveno DEX
A community-funded Monerocentric Bisq fork called Haveno is currently being developed and should soon be operational. Having a dedicated zero-KYC DEX (decentralized exchange) will greatly increase user privacy while substantially offsetting the negative effects of CEX delistings. Permissionless P2P trading is the future.
Haveno will utilize 2/3 multisig and atomic swaps. Users will be able to anonymously trade Monero ↔ Bitcoin and other cryptocurrencies as well as buy or sell Monero directly via bank deposit or cash-in-mail.
Where can I download the Monero wallet?
There are multiple Monero wallets for a wide range of devices at your disposal. Check the tables below for details and download links.
Attention: for extra security make sure to calculate and compare the checksum of your downloaded files when possible.
Please note the following usage of the labels:
![]() - Relatively new and/or beta. Use wallet with caution.
- Relatively new and/or beta. Use wallet with caution.
![]() - Closed source.
- Closed source.
Desktop wallets
| Wallet | Device | Description | Download link |
|---|---|---|---|
| “Official” GUI / CLI | Windows, macOS, Linux | Default implementation maintained by the core team. Use this wallet to run a full node and obtain maximum privacy. Integrates with hardware wallets. Current version: 0.17.2.3 - Oxygen Orion. | GetMonero.org |
| MyMonero | Windows, macOS, Linux | Lightweight wallet – you don’t need to download the blockchain and run a node. MyMonero was developed with the assistance of the core team. It also has web-based and iOS versions. | MyMonero.com |
| Feather | Windows, macOS, Linux | The goal of Feather is to provide a simple/easy-to-use Monero wallet for every day use. It is beginner friendly, but should also cater to the needs of experienced Monero users. Feather is designed with lower-specced hardware in mind. No fancy graphics or animations, runs well on virtual machines and with live operating systems. | FeatherWallet.org |
| Exodus | Windows, macOS, Linux | Exodus.io | |
| ZelCore | Windows, macOS, Linux | Zelcore.io | |
| Guarda | Windows, macOS, Linux | Guarda.co |
Mobile wallets
| Wallet | Device | Description | Download link |
|---|---|---|---|
| Monerujo | Android | Integrates with Ledger (hardware wallet). Website: https://www.monerujo.io/. | Google Play / F-Droid / GitHub |
| MyMonero | Android / iOS | Website: https://mymonero.com/ | Google Play / App Store |
| Cake Wallet | Android / iOS | Website: https://cakewallet.io/ | Google Play / App Store |
| Edge Wallet | Android / iOS | Multi-asset wallet. Website: https://edge.app/ | Google Play / App Store |
| ZelCore | Android / iOS | Google Play / App Store | |
| Coinomi | Android / iOS | Google Play / App Store | |
| Moxi / Guarda | Android / iOS | Google Play / App Store | |
| Exa Wallet | Android / iOS | Google Play / App Store | |
| Wookey Wallet | Android / iOS | Google Play / F-Droid / App Store | |
| Exodus | Android / iOS | Google Play / App Store |
How long does it take for my balance to unlock?
Your balance is unlocked after 10 confirmations (which means 10 mined blocks). A block is mined approximately every two minutes on the Monero network, so that would be around 20 minutes.
How can I prove that I sent a payment?
The fastest and most direct way is by using the ExploreMonero blockchain explorer. You will need to recover the transaction key from your wallet (complete guide for GUI / CLI).
Why I can’t see my balance? Where is my XMR?
Before any action there are two things to check:
- Are you using the latest available version of the wallet? A new version is released roughly every 6 months, so make sure you’re using the current release (compare the release on GetMonero.org with your wallet’s version on
Settings, underDebug info). - Is your wallet fully synchronized? If it isn’t, wait the sync to complete.
Because Monero is different from Bitcoin, wallet synchronization is not instant. The software needs to synchronize the blockchain and use your private keys to identify your transactions. Check in the lower left corner (GUI) if the wallet is synchronized.
You can’t send transactions and your balance might be wrong or unavailable if the wallet is not synced with the network. So please wait.
If this is not a sufficient answer for your case and you’re looking for more information, please see this answer on StackExchange.
How do I upgrade my wallet to the newest version?
This question is beautifully answered on StackExchange.
Why does it take so long to sync the wallet [for the first time]?
You have decided to use Monero’s wallet and run a local node. Congratulations! You have chosen the safest and most secure option for your privacy, but unfortunately this has an initial cost. The first reason for the slowness is that you will need to download the entire blockchain, which is considerably heavy (+70 GB) and constantly growing. There are technologies being implemented in Monero to slow this growth, however it is inevitable to make this initial download to run a full node. Consider syncing to a device that has an SSD instead of an HDD, as this greatly impacts the speed of synchronization.
Now that the blockchain is on your computer, the next time you run the wallet you only need to download new blocks, which should take seconds or minutes (depending on how often you use the wallet).
I don’t want to download the blockchain, how can I skip that?
The way to skip downloading the blockchain is connecting your wallet to a public remote node. You can follow this guide on how to set it up. You can find a list of public remote nodes on MoneroWorld.
Be advised that when using a public remote node you lose some of your privacy. A public remote node is able to identify your IP and opens up a range for certain attacks that further diminish your privacy. A remote node can’t see your balance and it can’t spend your XMR.
How do I restore my wallet from the mnemonic seed or from the keys?
To restore your wallet with the 25 word mnemonic seed, please see this guide.
To restore your wallet with your keys, please see this guide.
How do I generate a Ledger Monero Wallet with the GUI or CLI?
This question is beautifully answered on StackExchange. Check this page for the GUI instructions, and this page for the CLI instructions.
How do I generate a Trezor Monero Wallet with the GUI or CLI?
This question is beautifully answered on StackExchange. Check this page for the GUI instructions, and this page for the CLI instructions.
How can my local node become a public remote node?
If you want to support other Monero users by making your node public, you can follow the instructions on MoneroWorld, under the section “How To Include Your Node On Moneroworld”.
How can I connect my node via Tor?
This question is beautifully answered on StackExchange.
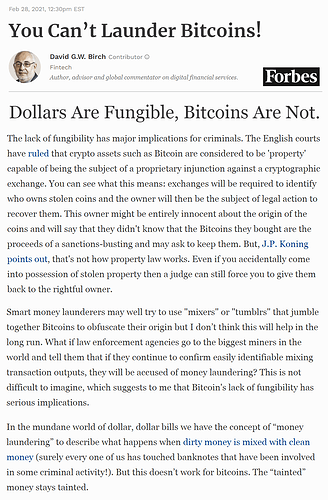
Bitcoin: The Original Non-Fungible Token
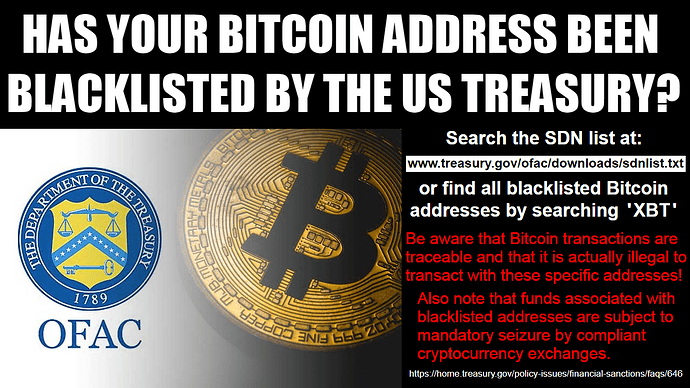
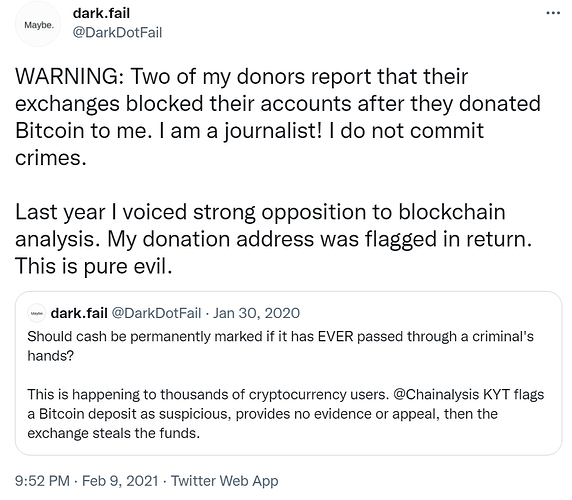
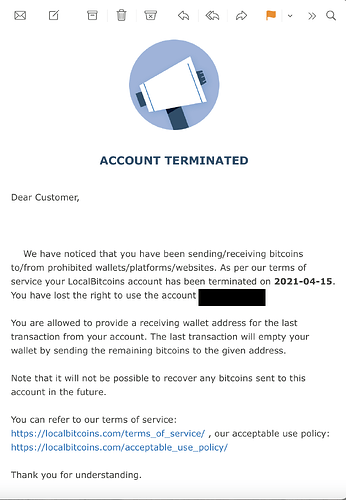
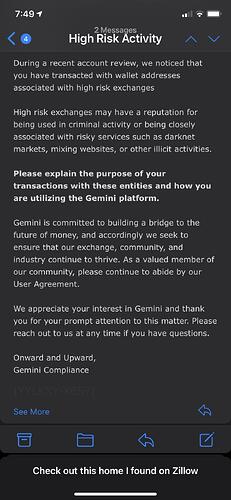
Bitcoin’s inherent lack of fungibility has real-world consequences: the US Department of the Treasury’s Office of Foreign Assets Control (OFAC) now maintains a blacklist of tainted digital currency (mostly BTC) addresses. Your funds can and will be seized if Uncle Sam decides they are somehow connected to sanctioned persons or associated “suspicious activity”.
How do I block digital currency?
Once it has been determined that your institution is holding digital currency that is required to be blocked pursuant to OFAC’s regulations, you must ensure that access to that digital currency is denied to the blocked person and that your institution complies with OFAC regulations related to blocked assets.
Blocked digital currency must be reported to OFAC within 10 business days. 202-622-2490 or ofac_feedback@treasury.gov
https://home.treasury.gov/policy-issues/financial-sanctions/faqs/646
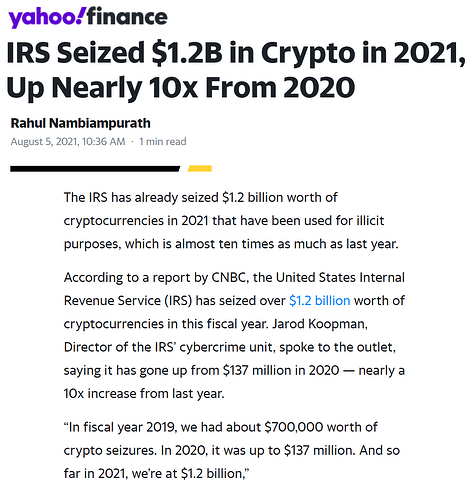
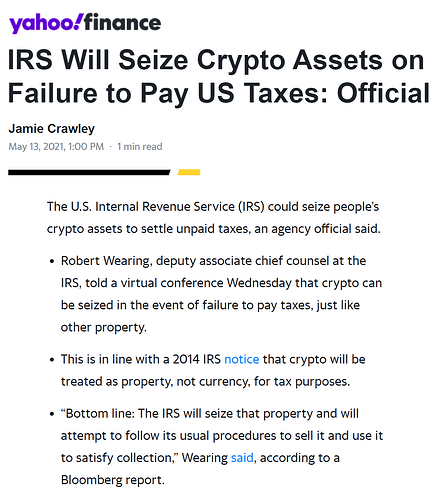
“Well, I’m not a criminal so I don’t have anything to worry about.” Actually, if the IRS decides you haven’t been paying them their fair share, they can now simply have Chainalysis process your blockchain history and then issue a seizure order. So in future make sure to say a Hail Mary before depositing your non-fungible coins on any compliant exchange!
Bitcoin’s fundamental inability to interface with legacy/KYC financial services without the potential for blacklisting and seizure looming over its users’ heads clearly brings its self-manifested “Store of Value” narrative into serious question. Since nobody will knowingly maintain a savings account with a bank that cannot guarantee sufficient cash reserves for withdrawals then why would anybody knowingly want to store their wealth in a cryptocurrency that cannot guarantee the fungibility required to make chain analysis and therefore coin seizure unfeasible?
And while Bitcoin’s privacy and thus fungibility will likely improve somewhat in future, “sorta” privacy retrofitted on top of a fundamentally transparent public ledger obviously will NEVER, EVER be as reliable as default full-spectrum privacy built from the ground up. Additionally, any added privacy functionality Bitcoin does get will still be optional, which, as the track record on optional privacy shows us, DOES NOT WORK since the average user tends to opt for the easy default settings, resulting in more transparent transactions that draw attention to and weaken the privacy guarantees of the fewer private ones. Expecting users to comprehend meticulous intracies in order to leverage a technology’s promised features is a significant design flaw.
Bitcoin maximalists tend to wave such concerns away with appeals to future development and the asinine assumption that the world is just going to sit and wait until the devs finally get it right. As Bitcoin’s slow death on the darknet is showing us, in the highly-competitive and ruthless world of fintech you either piss or you get knocked off the pot. Monero already works as fully fungible e-cash today and, judging by its exemplary developmental track record, its fundamentals will only get better over time.
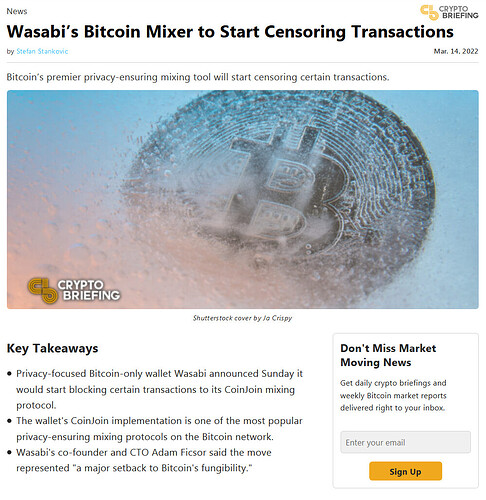
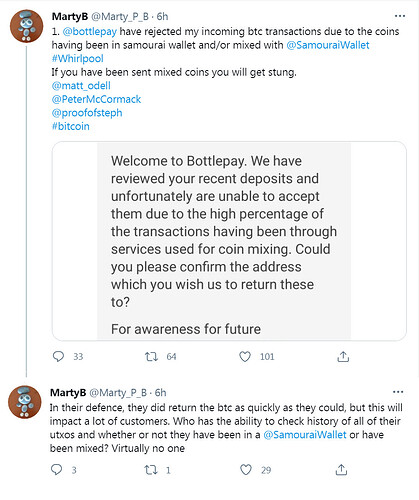
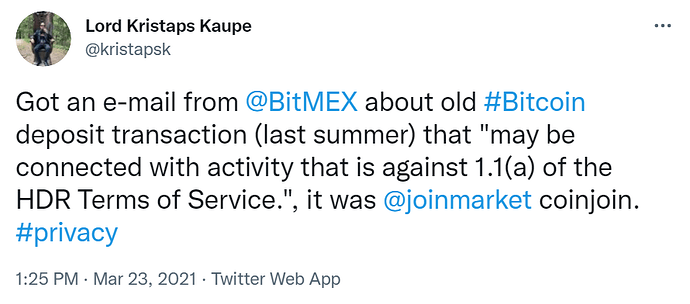
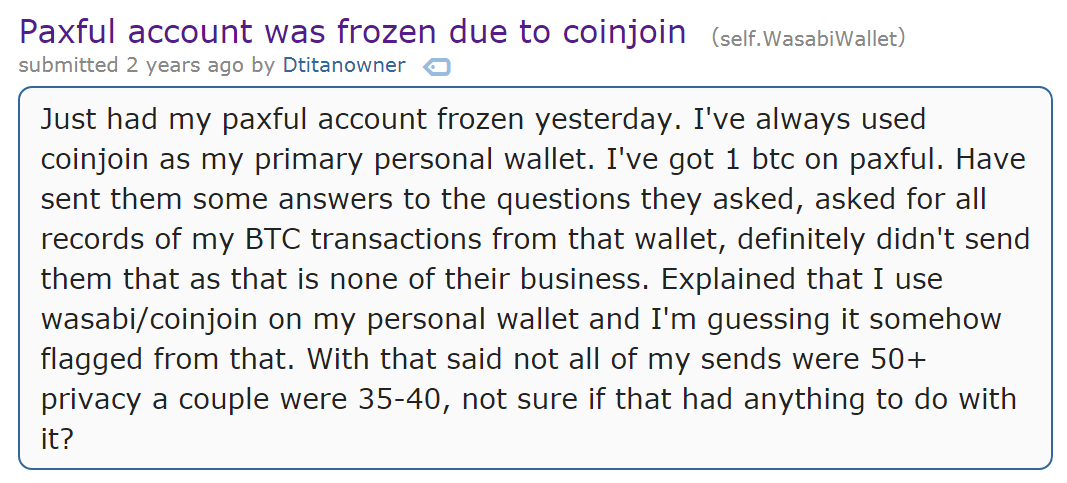
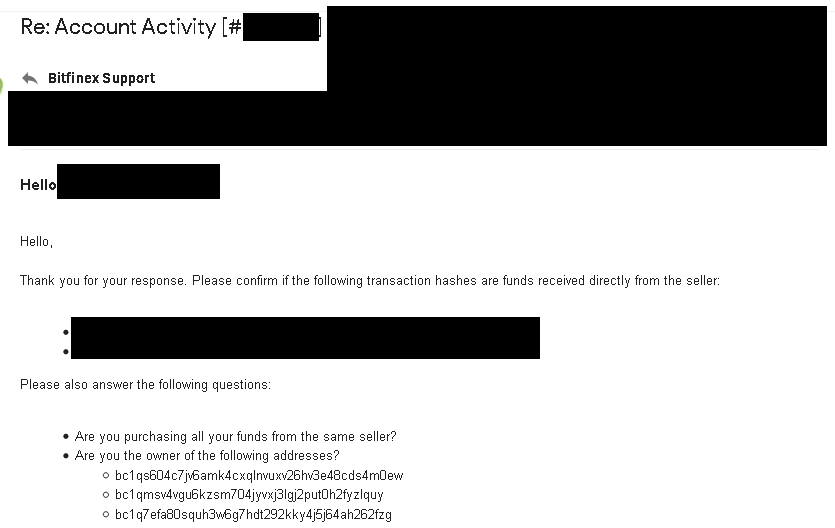
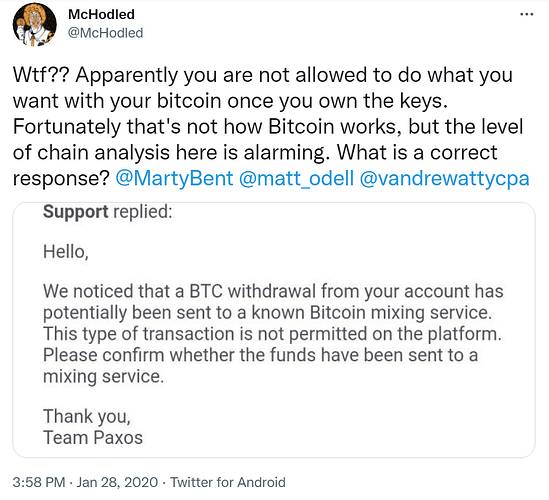
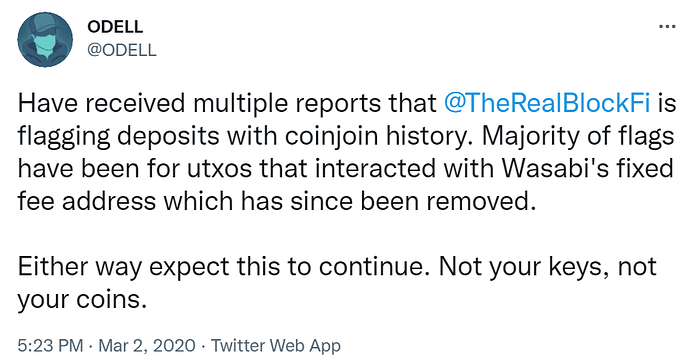
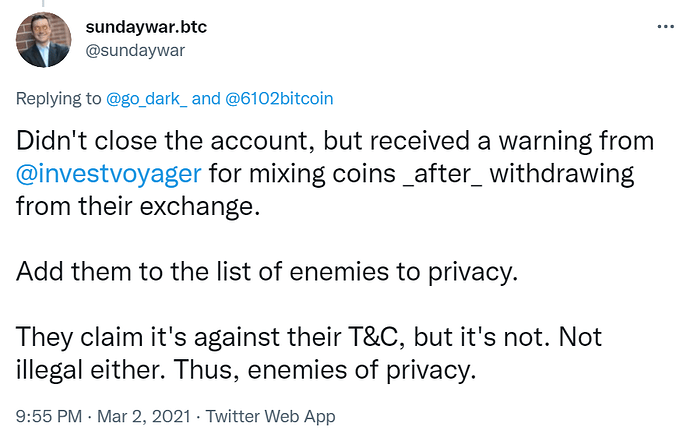
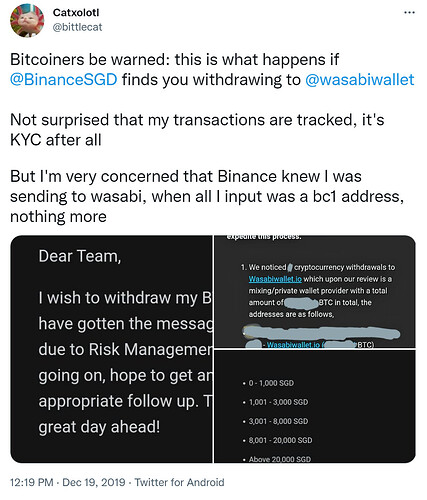
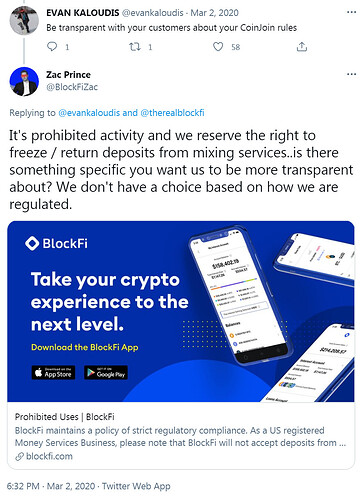
“Just use a mixer or CoinJoin, bro”
Binance Returns Frozen BTC After User ‘Promises’ Not to Use CoinJoin
https://cointelegraph.com/news/binance-returns-frozen-btc-after-user-promises-not-to-use-coinjoin
Major Exchange Restricts Crypto Transactions Linked to Coin Mixing, Sparking Privacy Concerns
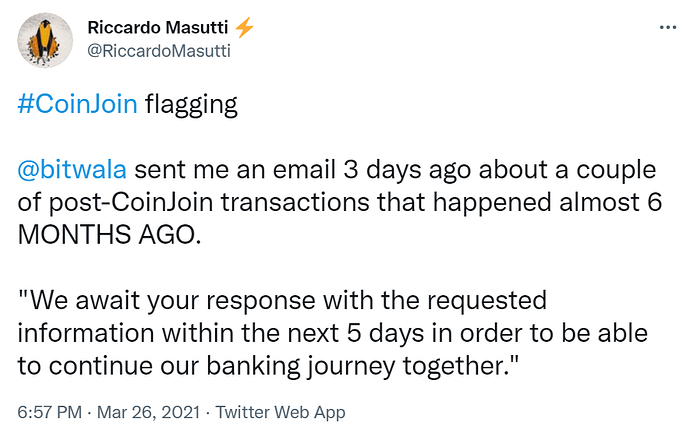
CoinJoin Flagging
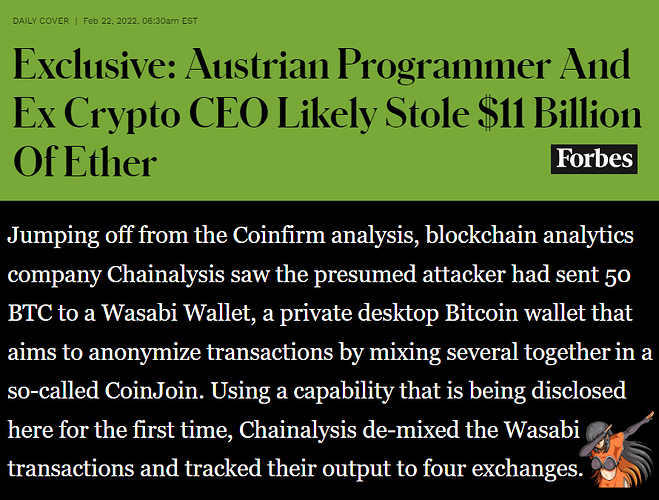
Money Trail From Liquid Exchange Hack Points to Wasabi Privacy Wallets
Although Wasabi is a non-custodial wallet that doesn’t store users’ funds, it generates addresses for CoinJoin transactions that blockchain analytics tools have learned to identify. Crypto sleuthing firm Elliptic did this last year, following bitcoin coming from the infamous Twitter hack to addresses associated with Wasabi.
Bitcoin’s Fungibility Graveyard
“Taproot and Schnorr will fix that, bro”
No, Taproot and Schnorr signatures most definitely will NOT make Monero redundant, due to its fundamental transparency Bitcoin can never and will never be as airtight as Monero.
Bitcoin Will Never Be Truly Private Says Andreas Antonopoulos: “Bitcoin is not a privacy coin”
“I think what we’re going to see soon is Schnorr, Taproot, and Tapscript, which open the door to a lot of improvements,” Antonopoulos said, “But they still do not involve zero-knowledge proofs or the types of ring signatures and stealth addresses that are done in Monero. Bitcoin is not a privacy coin.”
https://cointelegraph.com/news/bitcoin-will-never-be-truly-private-says-andreas-antonopoulos
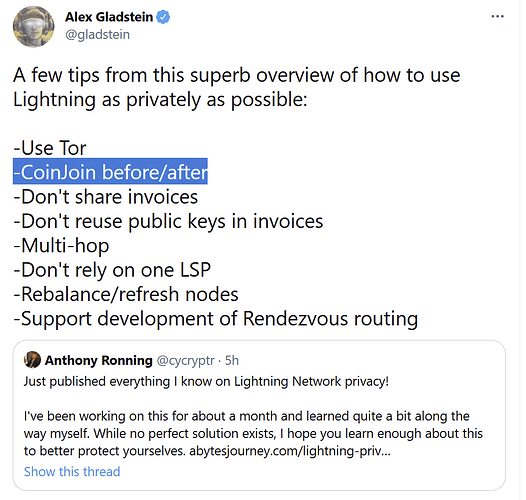
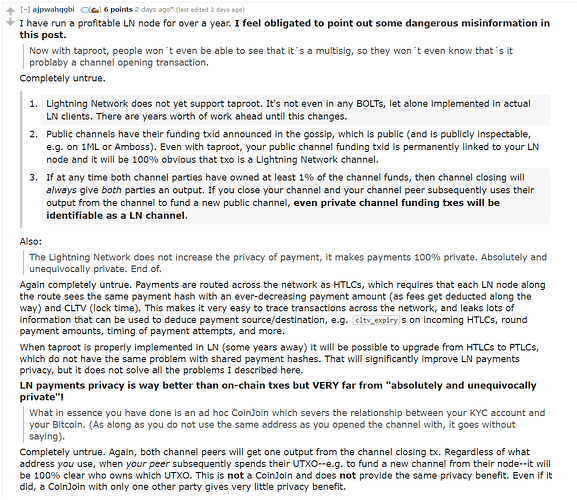
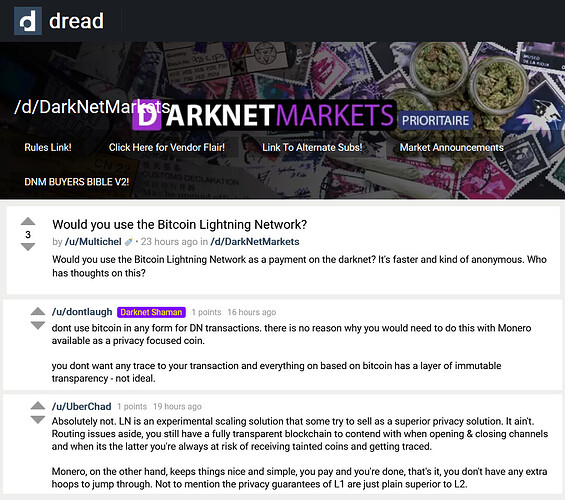
“Just use Lightning Network, bro”
No, Lightning Network also most definitely will NOT make Monero redundant, privacy as an afterthought on Layer 2 will never pass darknet-tier OPSEC muster on account of the increased attack surface. Another layer = added complexity = larger attack surface = greater statistical likelihood of exploits and data leakage, which can be used for heuristic attacks. Therefore, robust Layer 1 privacy will always be prioritized by those who require the best possible privacy guarantees.
Attack surface aside, Lightning Network also has inconsistent privacy guarantees to begin with. Users are still advised to CoinJoin both before and after and to keep other considerations in mind i.e. yet more things to worry about getting just right. Meanwhile, Monero users simply hit [send] and are done with it all.
“The important thing we need to achieve in the base layer is not scaling; the important thing we need to achieve in the base layer that CAN NOT be achieved in the layers above is fungiblity and privacy with strong guarantees and simple primitives. And if we have privacy primitives and fungibility primitives in the base layer than we can do scaling in the second layer and we can do it securely. Otherwise, we have a privacy problem. And that privacy problem will get magnified as we go up the layers. If you can do analysis on the base layer, that gives a great degree of insight into what’s happening above.”
Andreas Antonopoulos Bitcoin Q&A: Layered Scaling and Privacy
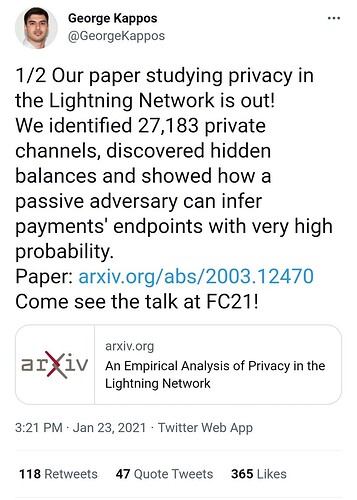
Researchers Surface Privacy Vulnerabilities in Bitcoin Lightning Network Payments
Current State of Lightning Network Privacy: “Unfortunately, there are scenarios where Lightning is not great for privacy”
"Sorry to burst your bubble, Lightning is a friends-only, nothing-can-ever-go-wrong toy network right now. The adversarial screws haven’t even been installed yet, let alone tightened. It’s time to wake up out of the hype dream.
There are two main classes of privacy attacks that really concern me, and as I will get into shortly are not just hypothetical things. They are very possible attacks with very real economic incentives that will inevitably create entities in the perfect position to exploit these classes of attacks."
Even these guys realize that optimal Bitcoin privacy still isn’t as reliable as just using Monero
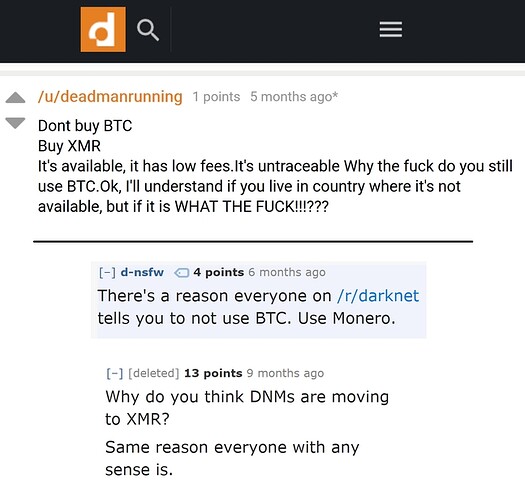
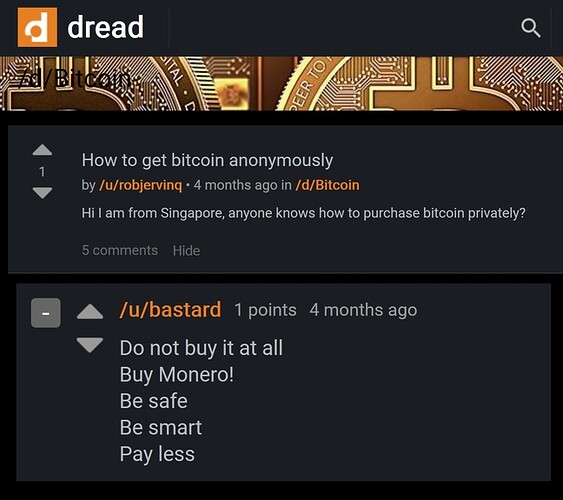
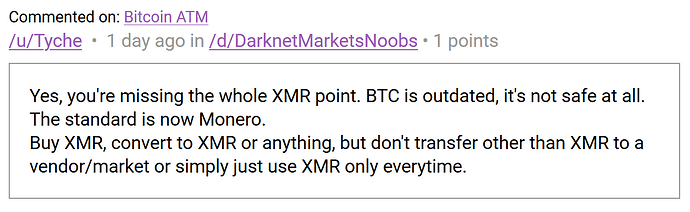
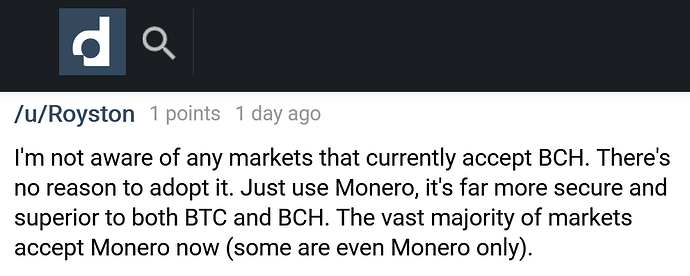
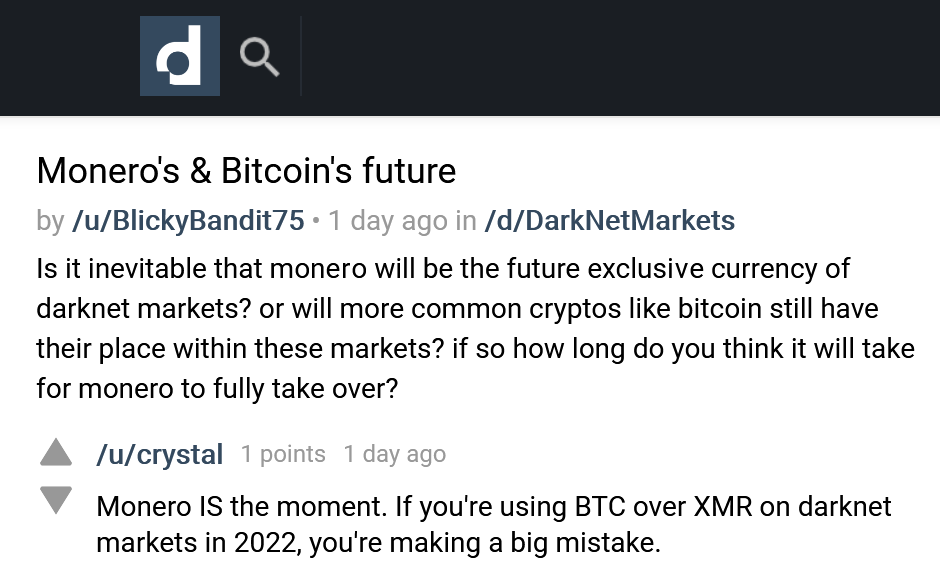
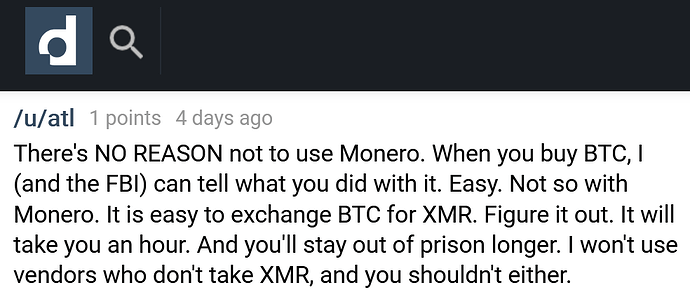
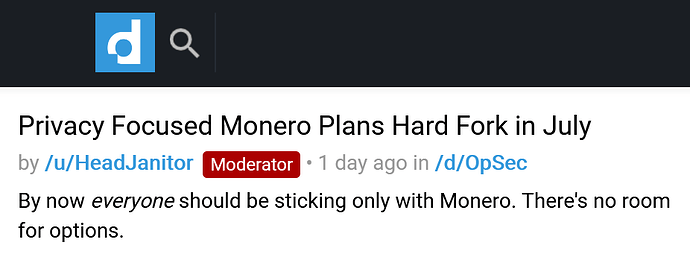
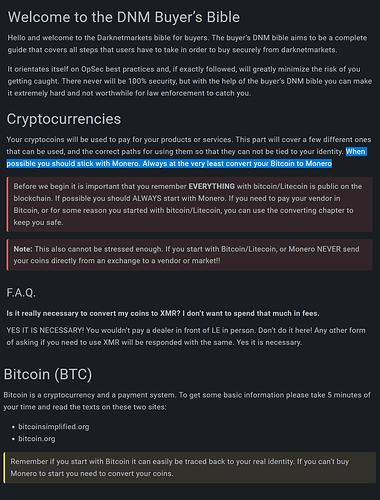
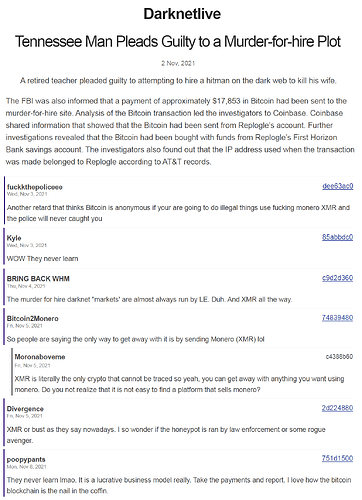
The darknet: where for obvious reasons you will repeatedly get told to ditch Bitcoin and start using Monero
Outside perspectives on Bitcoin
Ray Dillinger (worked with Satoshi): “Bitcoin is a disaster”
2021 expert analysis: “Bitcoin is easier to trace than traditional banking transactions”
Investment strategist and ex-HODLer: “Bitcoin is an investment cult”
Distinguished economist Steve H. Hanke: Bitcoin will be replaced by a superior crypto
Memetics Dept.
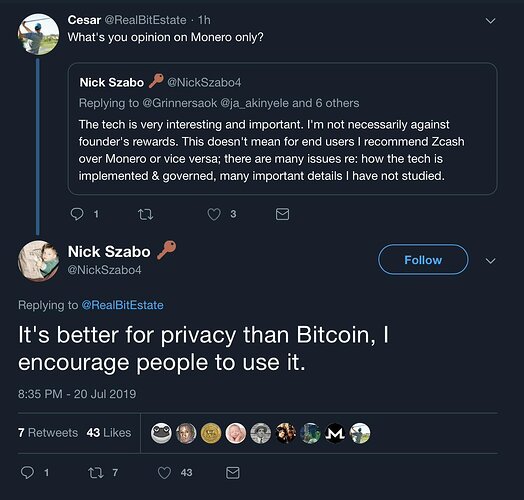
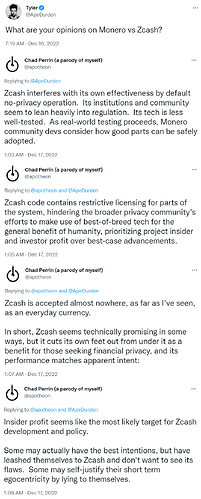
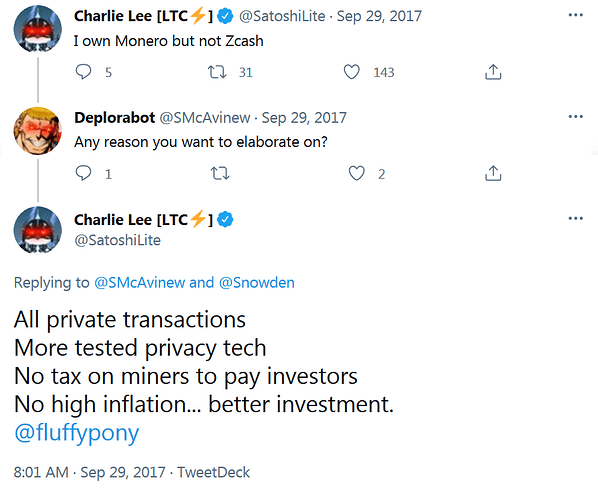
Why Monero is better than Zcash™

, all transactions look the same, transparency is strictly opt-in
- auto-shielded IP addresses
- uses established, well-understood, battle-tested and thus reliable cryptography as opposed to novel, experimental, much less understood and thus potentially flawed cryptography i.e. no “spooky moon math”
- modular approach to privacy = no single point of failure
- proven track record, 6+ years of sustained darknet usage with 0 users traced, has notably foiled the FBI, Europol & the IRS
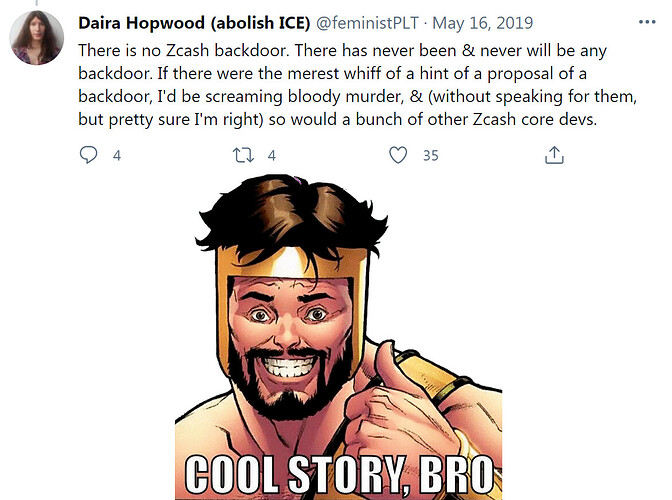
- no suspected backdoors
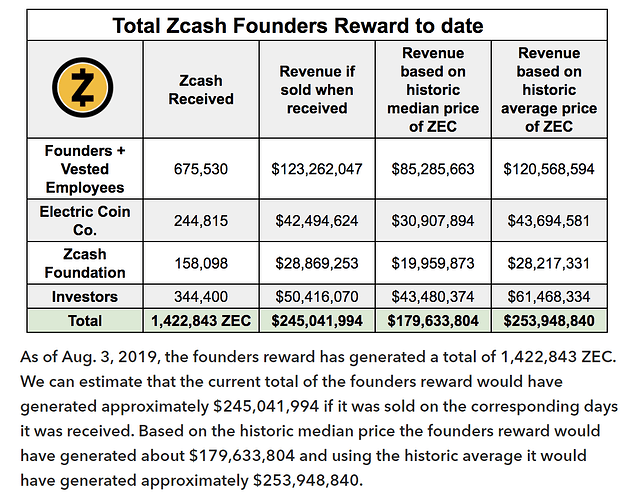
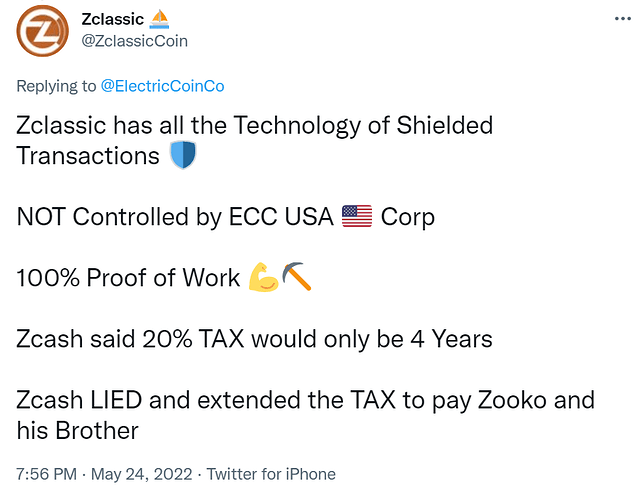
- no dev tax i.e. “founder’s reward/community development fund”, conditional donation-based dev funding gives the community more leverage and keeps devs disciplined
- wasn’t designed to systematically enrich founders & early Zerocoin Electric Coin Company LLC investors, whales either mined or bought their coins like everybody else
- not a Bitcoin fork
- not transitioning to Proof-of-Stake, PoW has a proven 10+ year track record while consumer-grade CPU mining remains the most anonymous, most permissionless way of acquiring coins
- ASIC resistance
- tail emission
- dynamic blocksize
- lower inflation
- ever-increasing real-world adoption, actually displacing Bitcoin in OPSEC-critical markets, endorsed by the DNM Bible
- growing criminal adoption = infinitely more street cred + law enforcement/regulator hostility = additional battle-hardening
- passionate grassroots enthusiasm, considerably more community engagement and activism, has better memes
- significantly better reputation, widely admired and respected by non-hodlers, has much more traction on Reddit, 4chan, etc
- greater decentralization = much more likely to survive a governmental crackdown on privacy coins
- no trademark restrictions, no pandering to the Establishment, has steadfastly remained true to crypto’s anti-authoritarian free market cypherpunk ideals
Meet the boss
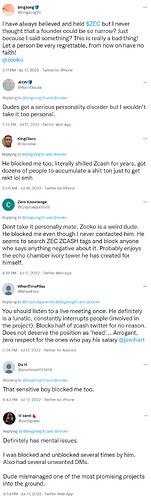
2018 article that shines a light on some seriously questionable activity regarding Zcash™’s governance
Zcash™ considering a move to Proof-of-Stake shows they prioritize wealth over privacy
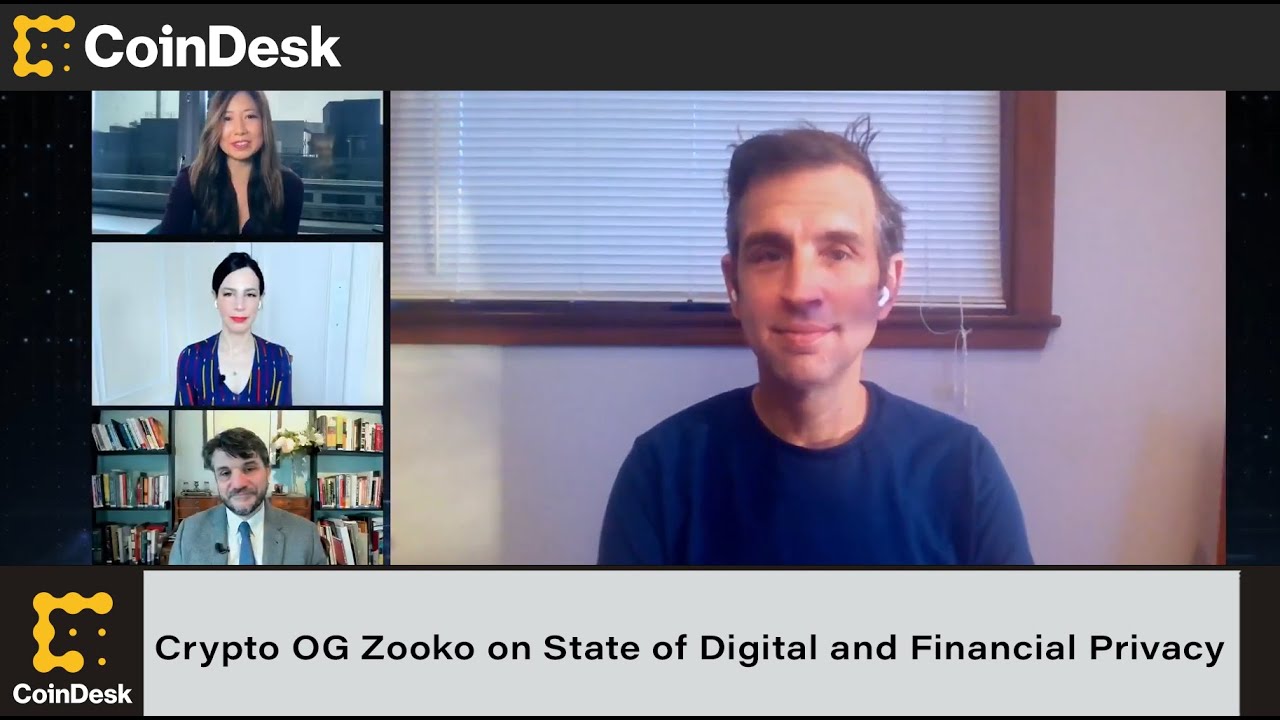
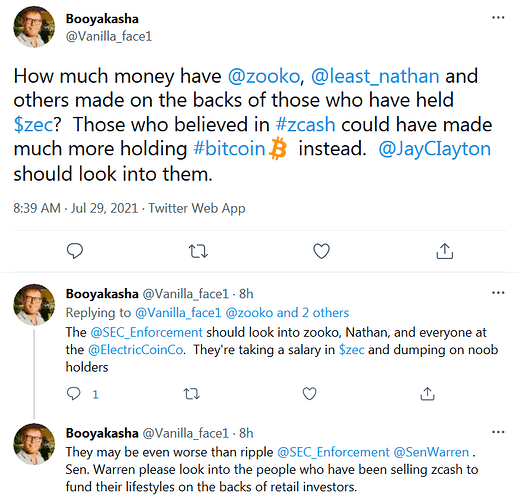
Zcash™ CEO gets paid circa $300K per MONTH while Monero’s core team works for free
https://www.coindesk.com/zooko-wilcox-ohearn-zcash-millionaire
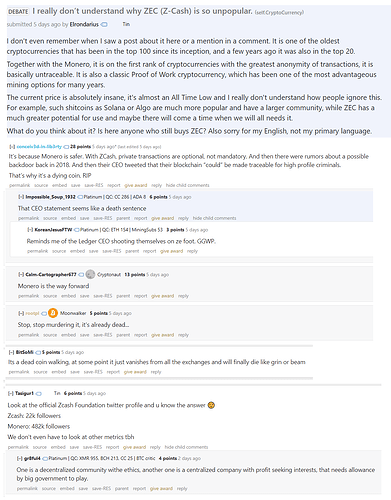
Bag-holding billionaire is surprised that Zcash™ is disliked by so many people, doubles-down to get a pump going
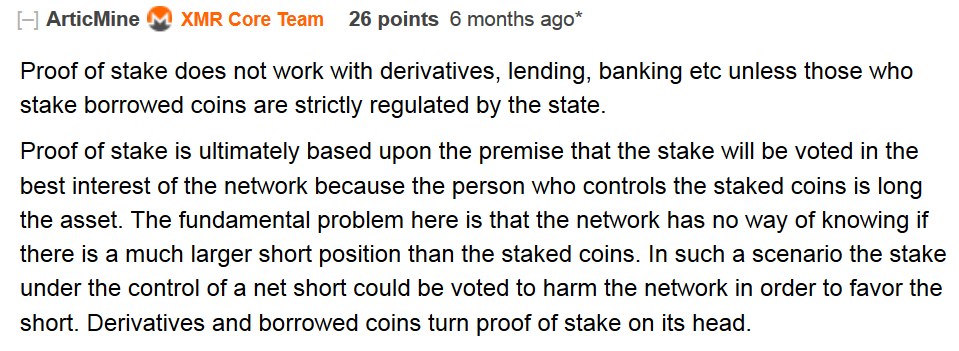
Why Proof-of-Stake privacy coins are a bad idea
- With PoS there is no way to buy into the network purely by mining. Mining is THEE most private way to independently acquire crypto, so with that option gone you are left relying on other holders to sell to you, which introduces an element of dependency and thus renders the process less permissionless and less private. Conversely, with (ASIC-resistant) PoW anybody with a computer can anonymously start mining for new coins.
- Law enforcement agencies tend to have a specific policy of not liquidating any privacy coins i.e.“Anonymity-Enhanced Cryptocurrencies” found in seized crypto wallets, ostensibly to prevent them from being used for nefarious activities. While this might actually be beneficial for a PoW privacy coin since it effectively reduces the available supply, it is potentially problematic for a PoS privacy coin because it gives historic adversaries the opportunity to stake seized coins and thus to acquire undue influence on network consensus. With PoS, the more coins that an entity holds, the more power and rewards they will earn. They can then use these rewards to keep increasing their stake, thereby achieving yet more influence over the network, which obviously defeats the goal of decentralization that cryptos seek to achieve.
TL;DR: a legitimate privacy coin will uncompromisingly seek to maximize privacy, permissionlessness & decentralization in all aspects. Using PoS is not consistent with this approach.
Predictably, a Zcash™ fork that seeks to address these flaws was launched by disappointed ZODLers
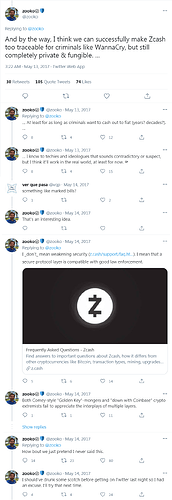
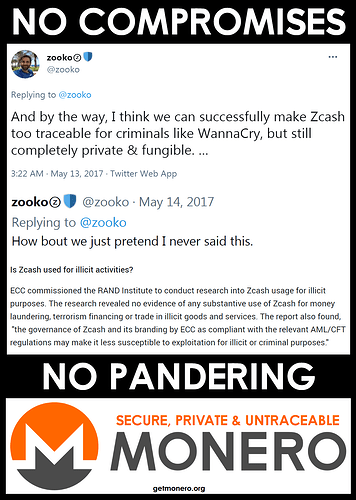
Zcash™ is toxic to criminals…and here’s why that’s a GOOD thing!
Because nothing says “decentralized cypherpunk ethos” like a Board of Directors
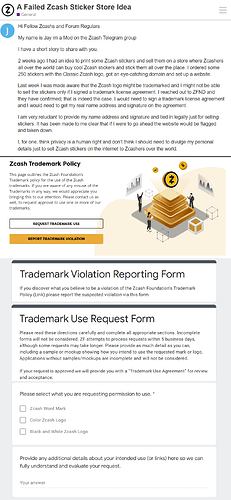
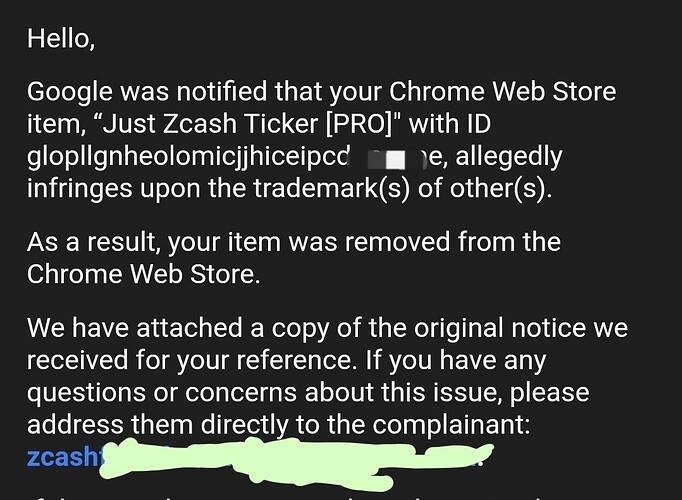
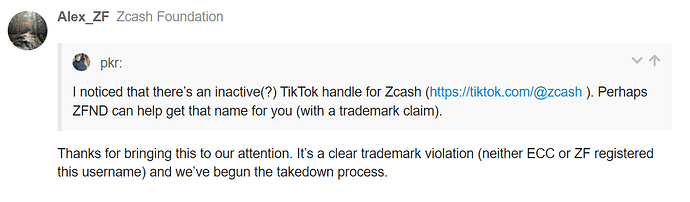
More corporate bullshit: you can’t use the Zcash™ logo without getting permission from their legal dept first
Think they won’t get ya? Fuck around and find out
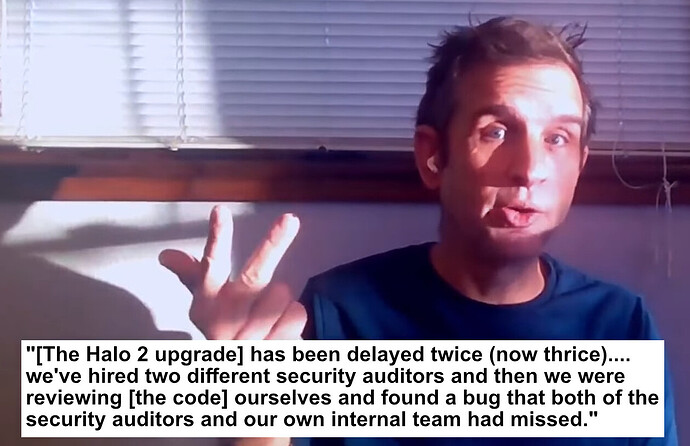
Unlike Monero, Zcash™’s tech is still so new and unproven it comes with specific disclaimers
A key hallmark of such exotic cryptography is poor peer comprehension, which makes detecting potentially devastating bugs much more difficult
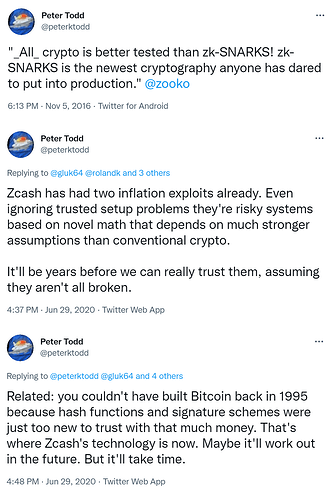
Bitcoin core dev Peter Todd has been warning about the potential hazards of Zcash™’s experimental tech (zk-SNARKs) for years
To his credit, at least the CEO has been upfront about it
Bottom line: older, widely used and more battle-tested cryptography is always going to be the safest, most reliable option
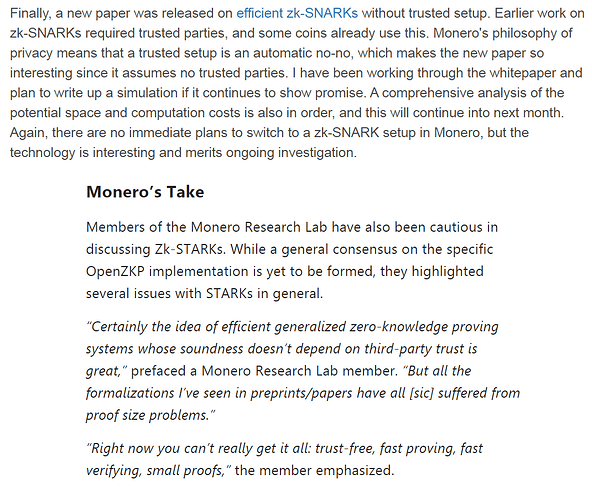
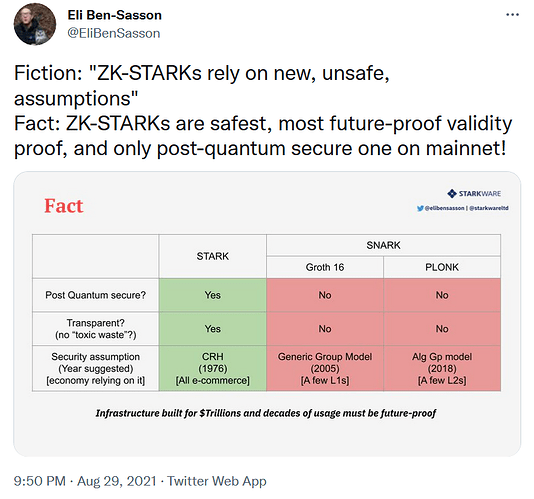
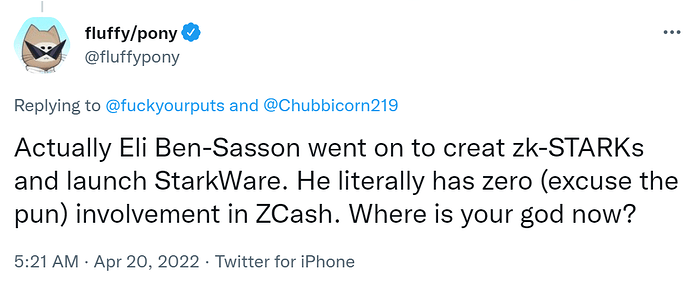
The advent of zk-STARKs will ultimately make zk-SNARKs less relevant
zk-STARKs are essentially a faster and much safer improvement on zk-SNARKs. They began being developed soon after Zcash™ launched by the same ZKP guru that co-invented zk-SNARKs, Eli Ben-Sasson. Eli cashed in his ZEC bags and went off to co-found StarkWare with another zk-SNARKs co-inventor, Alessandro Chiesa. StarkWare have been developing zk-STARKs ever since and are currently optimizing them in preparation for more widespread adoption.
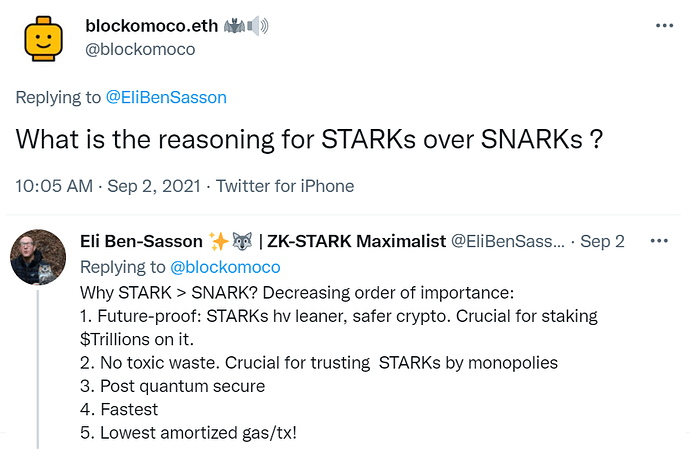
So what exactly is the big deal? With regards to the aforementioned concerns, STARKs are significantly safer than SNARKs since they utilize established collision-resistant hash functions that have been around since the late 1970’s. This makes STARKs less complex, highly predictable and therefore very reliable, they don’t require the kind of disclaimers that Zcash™ must add. Furthermore, STARKs have 20x faster proving times and, unlike SNARKs, they are fully quantum-resistant, which makes them the more future-proof option.
It’s very telling that Eli now identifies as a zk-STARK maximalist and only ever mentions zk-SNARKs to express his belief that they will be outperformed and obsoleted by zk-STARKs within the next 5 or so years.
It’s worth reminding that zk-STARKs have been on Team Monero’s radar practically since day one and they remain a primary candidate to someday replace ring signatures and improve overall scaling.
Sad day for you: Z-Cucks are butthurt over Eli and Alessandro ditching them for pastures greener
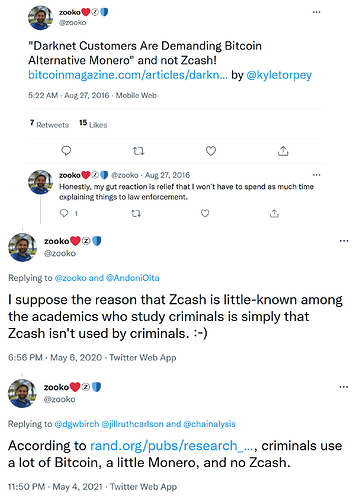
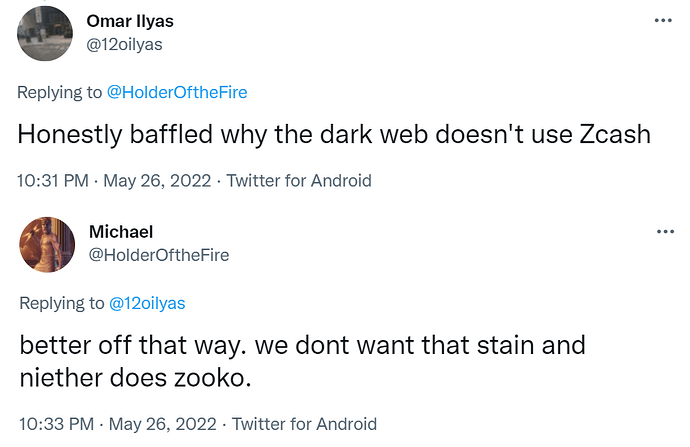
Zcash™ CEO is fanatical about compliance and kowtowing to regulators, actually gets triggered by the mere suggestion of darknet adoption instead of recognizing the critical validation that would bring
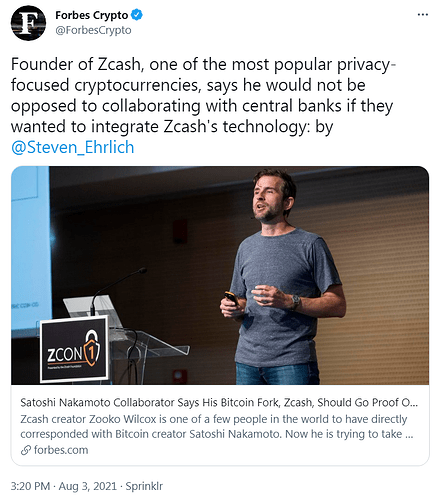
Instead of fighting them, Zcash™ CEO is willing to collaborate with central banks to aid the development of CBDCs
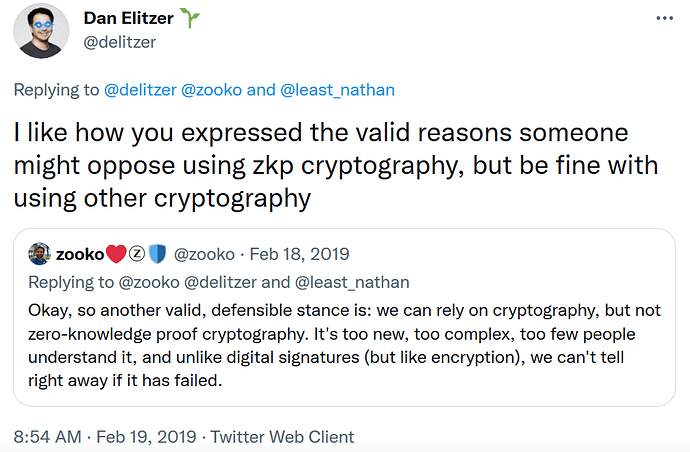
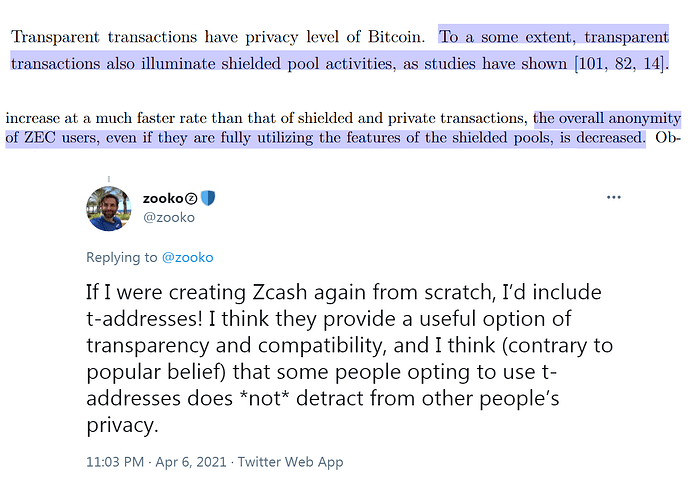
Zcash™ CEO insists optional privacy is preferable and not detrimental despite academic research repeatedly showing otherwise
zk-SNARKs are still very new, experimental and enigmatic technology that could yet be proven defective. Much more, years more peer review + battle-testing is necessary
Like their CEO, Z-Cucks have an almost pathological fetish for submitting to authority
This Is What Z-Cucks Actually Believe
Surprisingly, nobody on /biz/ is excited about Zcash™
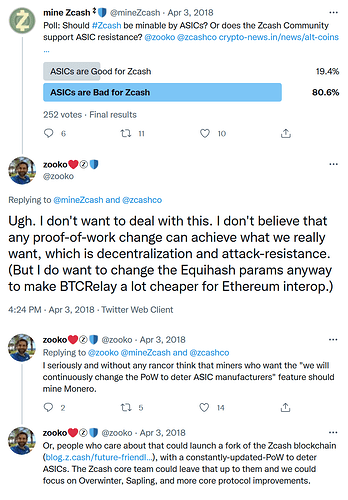
Zcash™ CEO doesn’t think ASIC resistance is something worth fighting for
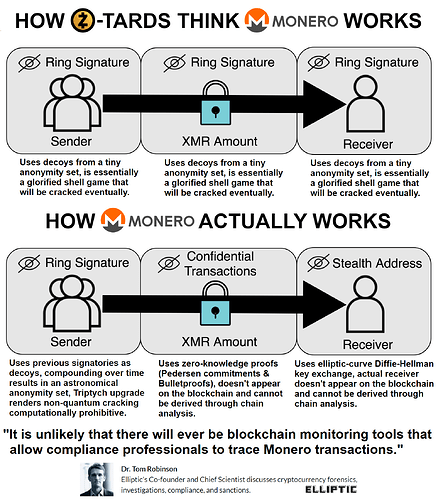
Muh decoys: Z-Tards don’t understand how Monero actually works
Predictably, Z-Cucks Can’t Meme

Memetics Dept.
The Lowdown on PirateChain
Premine shenanigans aside, it should also be noted that PirateChain is actually an asset chain of Komodo which is itself a fork of Zcash™ , meaning PirateChain inherits many of Zcash™’s liabilities and is dependent on Zcash™ for the majority of current and future core (zk-SNARKs) development. In other words, if Zcash™ sinks, PirateChain also goes down with the ship.
PirateChain’s primary selling point is that it uses zk-SNARKs and, unlike Zcash™, that it is fully private by default i.e. transparent transactions are disabled. While that definitely makes it preferable to Zcash™ privacywise, the theoretically superior privacy that zk-SNARKs offer is offset by their novelty and immaturity, which makes their reliability more questionable than older, more established tech. Namely, newer and insufficiently tested cryptography like zk-SNARKs carries with it risks of systemic failure that cannot be mitigated without years, typically decades worth of peer review and battle-testing, especially given the insane levels of mathematical complexity involved i.e. “moon math.” This is why some cryptographers would not be surprised if zk-SNARKs ultimately end up proving defective on account of some yet-undiscovered fatal flaw. Only time will tell.
Like Zcash™, PirateChain is also highly vulnerable to spam attacks. An attack costing just $0.45 was able to bring the network to its knees, cripple wallet software, and revealed that the network couldn’t even handle 10% of its claimed capacity of 31 transactions per second. At the time of writing, this vulnerability STILL has not been fully patched. Most of PirateChain’s “largest anonymity set of any cryptocurrency” is comprised of spam.
Also worth highlighting is that PirateChain’s bold claims of an invulnerability to 51% attacks (as dPOW tends to be advertised) are essentially a marketing ploy also borrowed from Komodo’s dodgy playbook. A security model that truly provides such an impressive degree of protection would obviously be adopted by every other chain in existence, the fact that nobody else is using it tells you everything you need to know.
Why dPOW is hot air
Shockingly, it turns out Komodo’s lead dev jl777 has a sordid history of assorted shenanigans and accusations of him being a scammer date back as far as 2014.
Furthermore, PirateChain’s claims of being “the world’s most private crypto” are also misleading since it’s TX volume is tiny in comparison to Monero, meaning it has a smaller overall anonymity set so correlation attacks are easier to execute, statistically you still get better privacy using Monero.
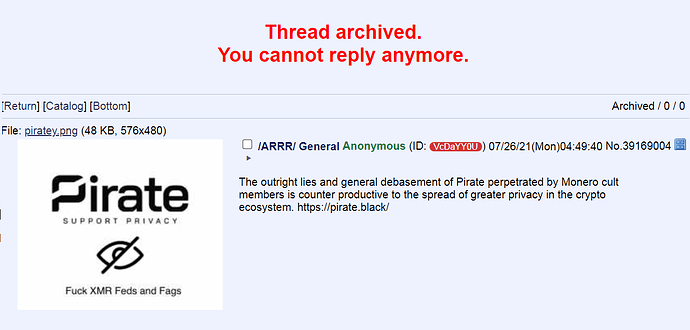
Predictably, the darknet crowd doesn’t take PirateChain seriously at all and prefers Monero by a vast margin
Like its big brother Zcash™, nobody on /biz/ is excited about PirateChain either
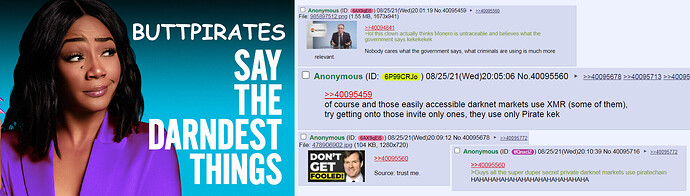
ButtPirates have very vivid imaginations
No, the darknet still isn’t interested, silly ButtPirates!
Memes sourced from 4chan, Twitter & XMRmemes.com
Tip Jar
89pw9u2ZcUcHwWns3vzd9Ng2fi7FHEhbecKfSmtSxRAb7t9Wg4MMtoZJdgBzyFwm96Q1Gdrtp8uaVZDGz4ovvLtGEuFDKd2